










Blockchain Dark Forest Self-Rescue Manual
There are thousands of blockchain roads, but safety always comes first.
Tags:A must-see for beginnersIntroduction
First of all, I want to congratulate you for seeing this manual. I don't know who you are, but if you hold cryptocurrency or are interested in this world and may hold cryptocurrency in the future, then this manual is worth reading repeatedly and practicing carefully.
Secondly, you need to be mentally prepared: reading this manual requires a certain knowledge background. I try to take care of beginners, but it is difficult. I hope beginners don’t have to be afraid of these knowledge barriers, because a lot of them can be “played”. If you encounter a knowledge point that you don't understand and need to expand your understanding, I suggest you use Google. And it is strongly recommended that you master aSafetyPrinciple: For knowledge on the Internet, refer to information from at least two sources for everything, support each other, and always remain skeptical.
Yes, always be skeptical! Include any knowledge points mentioned in this manual :)
BlockchainIt is a great invention. It has brought about changes in certain production relations and partially solved the precious problem of "trust". This is already rare. There is no need for centralization or third-party roles. Some "trust" can be well solved based on blockchain. It cannot be tampered with, is executed according to the agreement, and prevents denial. However, the reality is cruel. There are many misunderstandings about blockchain. These misunderstandings have led to bad guys easily taking advantage of loopholes and frequently reaching their black hands into people's wallets, causing a large amount of financial losses. This has long been a dark forest.
In the blockchain dark forest world, first keep in mind the following two majorSafetylaw:
1. Zero trust. Simply put, be skeptical, and always be skeptical.
2. Continuous verification. If you want to believe, you must have the ability to verify your doubts and develop this ability into a habit.
Note: In this manual, these two safety rules are the only ones. Others can be considered as safety principles deduced from these two.
Okay, that’s it for the introductory part. Let's start with a picture and enter this dark forest to see what risks we will encounter and how we should deal with them.
a picture
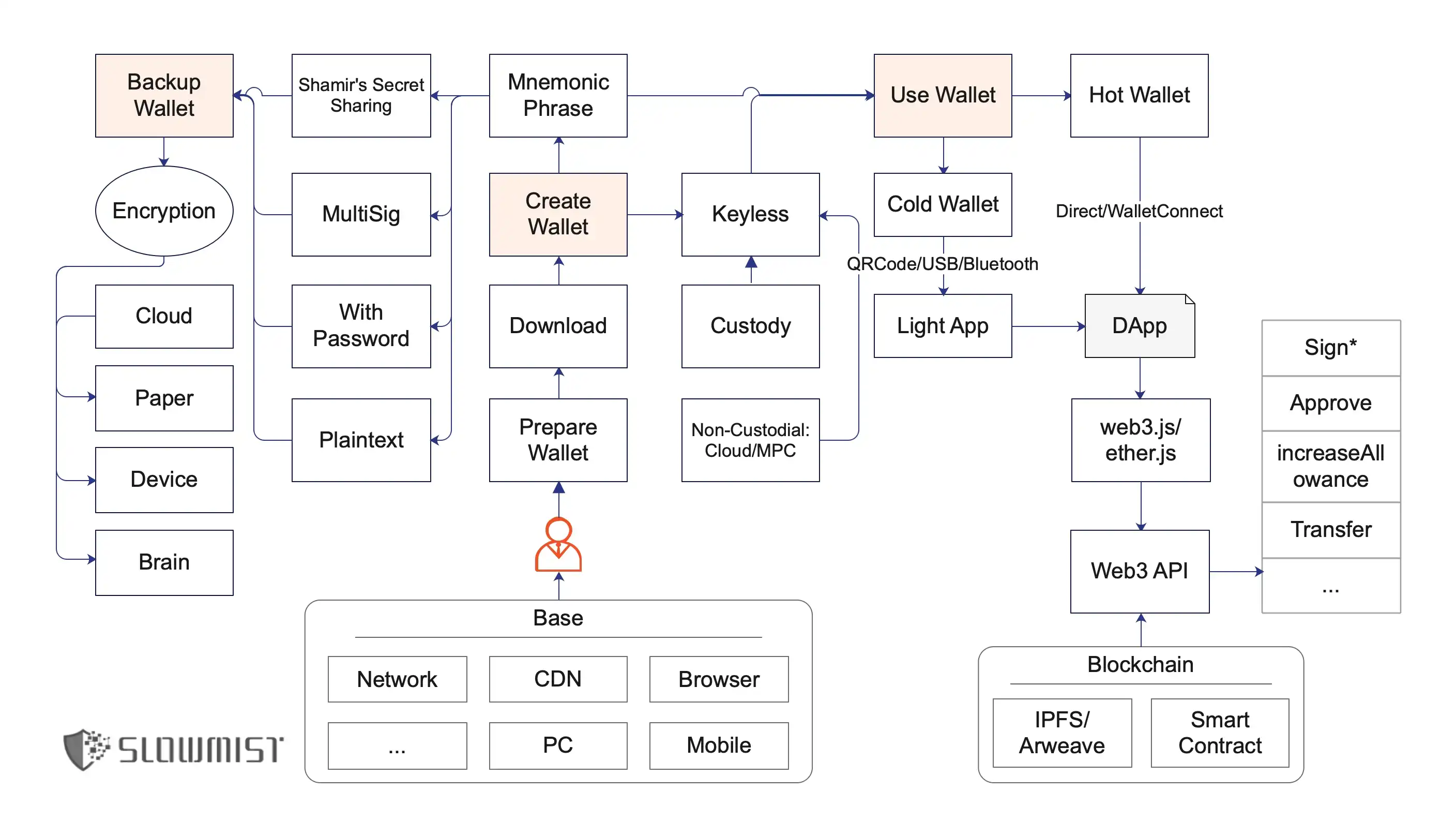
Before reading the following article in detail, you can take a rough look at this picture. This picture is about your key activities in this world (no matter what you call this world, blockchain, cryptocurrency or Web3). The process includes three parts: creating a wallet, backing up the wallet and using the wallet. .
We follow these three processes and analyze each key point involved.
Create wallet
The most important thing in the wallet is the private key (or mnemonic phrase).
The private key looks like this:
0xa164d4767469de4faf09793ceea07d5a2f5d3cef7f6a9658916c581829ff5584
The mnemonic phrase looks like this:
cruel weekend spike point innocent dizzy alien use evoke shed adjust wrong
Note: Using Ethereum as an example, please expand your basic knowledge about private keys/mnemonics by yourself.
The private key is the identity. If the private key is lost orsteal, then this identity is no longer yours. There are actually many wallet applications, and there are many well-known ones. I do not intend to and cannot introduce them one by one. However, the manual does mention some specific wallets. Please note that the mentioned wallets must be ones that I have basic trust. However, I do not guarantee that security issues that may arise during your use or that the target wallet may appear are not mine. Anticipated security risks (I won’t go into nonsense about these in the rest of the article. I hope you keep in mind the two major security rules mentioned in the introduction).
In terms of application classification, wallets mainly include several types: PC wallets, browser extension wallets, mobile wallets, hardware wallets and web wallets, etc. In terms of whether they are connected to the Internet or not, they can be mainly divided into cold wallets and hot wallets. When we want to enter this world, we must first think about the purpose of the wallet we will own. The purpose determines which wallet you will use, and the purpose also determines how you will treat this wallet.
No matter what wallet you choose, at least one thing is certain: after playing in this world for a long time, you cannot have only one wallet.
So here we need to remember another safety principle: isolation, that is, don’t put eggs in one basket. Generally speaking, the more frequently a wallet is used, the greater the risk of problems. Always remember: When facing a new thing, first prepare a separate wallet and use a separate small fund to play for a period of time. Unless you have been like me, experienced countless things, and know many things clearly. However, if you often walk by the river, how can your shoes not get wet?
· Download
Even something as simple as this is not simple at all, for the following reasons:
1. Many people (really many people) cannot find the correct official website and the correct application market, so they install fake wallets.
2. Many people don’t know how to confirm whether the downloaded application has been tampered with.
Therefore, he died before leaving the army. Before I even had time to enter this world, my wallet was already empty.
Regarding point 1 above, there are techniques to find the correct official website, such as:
· Industry-renowned inclusions, such as CoinMarketCap
· Ask more trusted people
Okay, the information obtained from the above points can be combined for reference and mutual support. In the end, there is only one truth:) Congratulations, you have found the correct official website.
Next, you have to download and install the application.If it is a PC wallet, according to the download link provided by the official website, you need to install it yourself after downloading. However, before installation, it is recommended to verify whether it has been tampered with. Although this method cannot prevent the source from being completely tampered with (such as the official doing evil internally, being hacked internally, the official website being invaded and replacing relevant information, etc.), However, it can prevent situations such as partial tampering of the source, hijacking and tampering by middlemen, etc.
The verification of whether it has been tampered with is actually a file consistency verification. There are two common ways:
· One is hash verification, such as MD5, SHA256, etc. MD5 is sufficient in most cases, but there is a minimal risk of hash collision, so the industry generally chooses SHA256, which is sufficient and safe.
· The other is GPG signature verification. This is actually very popular. It is highly recommended to master GPG tools, commands, and methods. Although it is a bit laborious for newcomers, once you get started, believe me, you will be very happy.
Having said that, there are actually not many project parties in the industry that do this, so once you encounter it, it is really rare and cherished. For example, a Bitcoin wallet Sparrow Wallet, the "Verifying the Release" on the download page is simply conscience, mentioned There are clear guidelines for both methods, you can refer to them directly:
There are two GPG tools mentioned on this page:
· GPG Suite, running under macOS.
· Gpg4win, runs under Windows.
If you observe carefully, you will find that the download related pages of these two GPG tools actually provide consistency verification instructions for the two methods, but unfortunately, they do not teach you how to verify. I guess they all think that you will be a smart person, and you have already made up for the knowledge you need to make up for:)
If it is a browser extension wallet, such as MetaMask, which is a household name in the world. The only thing you have the opportunity to pay attention to is the number of users on the target extension download page and the ratings. For example, MetaMask has more than 10 million users in the Chrome Web Store. At the same time, There are more than 2,000 user ratings, although the final rating is not high. Does anyone want to say that this can't be brushed out? This friend, it’s like this, swiping, I believe it, but the amount of swiping is so huge, it makes all parties think they are fools.
If it is a mobile wallet, the judgment method is similar to extending the wallet, but it should be noted that the iPhone App Store is partitioned, and cryptocurrencies are not well expelled in mainland China, so if you use the App Store China account to download the wallet, there is only one suggestion: don’t use it , change to the App Store account in Rumei District and download it. In addition, you can also be guided to the correct download location through the correct official website (such as the world-renowned imToken, Trust Wallet, etc. The security of the official website must be done well. If the official website is hacked, then the security responsibility is really huge).
If it is a hardware wallet, to put it simply, you can buy it under the guidance of the official website. Do not go directly to the online mall. After you get it, you need to pay attention to whether there have been any changes. Of course, some changes in hardware packaging are very clever, and not necessarily all can be seen. inferred. It is recommended at this time: No matter what, when using it, first create it from scratch at least three times in a row, record the generated mnemonic words and related wallet addresses, so as not to repeat them.
If it is a web wallet, it is strongly not recommended to use this kind of online wallet, unless you have no choice, then after identifying it is official, make a quick decision, and don't have any emotional dependence.
·Mnemonic Phrase
Generally speaking, after we create a wallet, the key information we deal with directly is the mnemonic (rather than the private key). After all, the mnemonic is convenient for humans to remember. There are standard conventions for mnemonics (such as BIP39), which puts forward requirements for mnemonics. For example, it is generally 12 English words. It can also be other numbers (multiples of 3), but it will not exceed 24 words. It must be Otherwise, it will be too complicated and will not be mnemonic. If the number is less than 12, the security will not be reliable. 12, 15, 18, 21, and 24 are all easy to say. However, judging from industry habits, 12-bit is generally popular and has sufficient security. Some hardware wallets with extremely strict security, such as Ledger, have 24-bit as standard. In addition to English words, it can also be other words, such as Chinese, Japanese, Korean, etc. But not all words can be used. There is a fixed list of 2048 words. For specific reference:
https://github.com/bitcoin/bips/blob/master/bip-0039/bip-0039-wordlists.md
When creating a wallet, the appearance of the mnemonic phrase is very sensitive. Please note that there are no people or cameras around you that could lead to peeping. At the same time, pay attention to whether the mnemonic phrase appears randomly enough. Normally, the random numbers of the mnemonic phrase generated by these well-known wallets are absolutely sufficient. Isn't this just in case? It’s really hard to know if there is anything fishy about the wallet you get. Don’t find it too troublesome. Once these little safety habits are formed, believe me, you will really be happy. Finally, in some scenarios, you may even consider disconnecting from the Internet to create a wallet, especially if you plan to use the wallet as a cold wallet. Disconnecting from the Internet is simply a violent aesthetic.
· Keyless
Keyless, as the name suggests, means no private key. Here we divide Keyless into two major scenarios (note that the distinction here does not represent the recognized distinction in the industry, it can only be said to facilitate my explanation):
Custody, that is, the custodial method. For example, centralized exchanges and wallets, users only need to register an account and do not own private keys. The security is completely dependent on these centralized platforms.
· Non-Custodial, that is, non-custodial mode. The only thing the user has is a private key-like power, but not a direct cryptocurrency private key (or mnemonic phrase). For example, relying on the well-known Cloud platform for hosting, authentication and authorization, at this time the well-known Cloud platform becomes the shortcoming of Cask. It also uses secure multi-party computation (MPC) to ensure that there is no single point of risk, and also combines with the well-known Cloud to provide the best user experience.
For me, I have used several Keyless methods. The centralized platform with strong strength and good reputation has a good experience, as long as it is not caused by its own reasons.stealIf the account-related permissions are stolen, these platforms will also cover the compensation. As for the Keyless solution based on MPC, I think it is very promising and should be popularized as soon as possible. I have used good ones such as (ZenGo, Fireblocks, Safeheron). The advantages are obvious. I will briefly mention a few points:
· MPC algorithm engineering practice is becoming more and more mature on these well-known blockchains, and it only needs to be carried out for private keys.
· A set of ideas can solve the problem of huge differences in multi-signature solutions in different blockchains and make them universal in user perception. This is what we often call: universal multi-signature.
· It can ensure that the real private key never appears and solve single point risks through multi-party calculation.
· Combined with the well-known Cloud (or Web2 as some people mentioned), MPC is not only secure but also has a smoother experience.
The advantages are obvious, but there are also disadvantages. I will briefly mention a few:
· It meets industry-recognized standards and is open source. The maturity in this area is far from enough, and everyone still needs to work hard.
Many people say that they basically only play with the Ethereum series (or EVM-based blockchains), so a multi-signature solution such as Gnosis Safe, a smart contract, is enough.
No matter which method is used, as long as you feel it is safe, controllable and comfortable to use, it is a good method. The wise have different opinions.
Okay, I will introduce these relevant security precautions when creating a wallet. Some general security issues will be introduced later, so don’t worry yet:)
Backup wallet
Many good people have fallen into this trap, including me. I often walk by the river and I recognize wet shoes. Fortunately, this is not a big asset wallet, and in the end my brother at Slow Mist helped me solve it. . This is also a great thing. I didn’t back up properly and I fell into a trap, but I have great resources that can help me solve this pitfall. But I also break into cold sweats, that’s human nature. You definitely don’t like the feeling of breaking into a cold sweat, so just focus on learning how to back up your wallet safely.
· Mnemonic phrase/private key type
What we call a backup wallet is actually a backup mnemonic phrase (or private key, for the convenience of introduction, only the mnemonic phrase will be mentioned below). The mnemonics we get can actually be divided into several types:
· plain text
· With password
·Multiple signatures
· Shamir's Secret Sharing, referred to as SSS
I will briefly expand on these types.
plain text, easy to understand, once you get those 12 English words, the assets inside are yours. In fact, you can consider making some special "shuffle rules" at this time, or even replace certain words with other words. Doing this will cause a headache for the bad guys, but if you forget this "law", it will be your turn to have a headache. Don’t think it’s impossible for you to have a headache. Believe me, after one, two, or five years, memory will really get messed up. A few years ago, when I was playing with the Ledger hardware wallet, I fell into a trap. There were 24 words in the mnemonic phrase. I messed up the order when I copied it for backup. A few years later, I forgot the ordering rules and couldn't remember whether I had replaced any of them. word. As mentioned before, my problem was later solved. A special cracking program collided with the correct mnemonic sequence and corrected several words.
with password, according to the standard, the mnemonic can be accompanied by a password. The mnemonic is still the same mnemonic, but after adding the password, you will get a different seed. This seed is used to derive a series of private keys and public keys later. and corresponding address. At this time, you must not only back up the mnemonic phrase, but also do not forget the password. By the way, in the form of password, in addition to the matching mnemonic, the private key also has related standards (such as BIP38), as well as Keystore files common in the Ethereum series.
Multiple signatures, it can be understood that the target funds need to be signed and authorized by multiple people before they can be used. Multi-signature is very flexible and you can set the approval policy. For example, if 3 people have keys (mnemonic words or private keys), they need to meet the signature approval of at least 2 people. The target funds can be used. Each blockchain will have its own multi-signature solution. The Bitcoin series is well understood. Well-known Bitcoin wallets natively support multi-signature. However, the Ethereum series mainly implements multi-signature through smart contracts, such as Gnosis Safe. In addition, in addition to these more common multi-signature schemes, there is another type that is becoming popular: MPC (Secure Multi-Party Computation), which is close to the traditional multi-signature experience, but the principle is very different. Through MPC, you can To achieve universal multi-signature, different multi-signature methods for different chains are not required.
SSS, Shamir secret sharing scheme, the function is to divide the seed into multiple fragments (commonly, each fragment has 20 words). When restoring the wallet, you need to use a specified number of fragments to restore. Please refer to industry best practices for specific reference:
https://support.keyst.one/v/chinese/gao-ji-gong-neng/zhu-ji-ci/chuang-jian-dao-ru-fen-pian-zhu-ji-ci
Using solutions such as multi-signature and SSS will actually give you a lot of peace of mind and avoid single-point risks, but the management is also relatively complicated, and it often involves multiple people. Convenience and security are eternal contradictions, it depends on yourself. But don’t be lazy when it comes to rules and principles.
· Encryption
Encryption is a very, very big concept. No matter whether it is symmetric, asymmetric or other advanced, as long as it is encrypted, you or your disaster recovery personnel can easily decrypt it after many years, and the encryption that cannot be decrypted by others is good. encryption.
According to the security rule of "zero trust", when we back up the wallet, every link must assume that it may be invaded, even the physical environment, such as a safe. Don’t forget, no one else in this world is completely trustworthy except yourself. In fact, sometimes you are not trustworthy either. For example, your memory may be faded or confused. But I wouldn’t assume the world is so scary, or I’d end up screwing things up.
Be sure to give special consideration to disaster recovery when backing up. Disaster recovery is mainly about avoiding single points of risk. What if you are gone? What if the environment where your backup target is located is gone? Therefore, important things must have disaster recovery personnel; important things must have multiple backups.
Well, I won’t talk nonsense about the choice of disaster recovery personnel. It depends on who you trust. I focus on multiple backups. Let’s first look at some basic forms of backup locations:
· Cloud
· Paper
·Device
· Brain
Cloud, many people talk about cloud backup. It seems that hackers really come and go without a trace. In fact, the offensive and defensive confrontation is always a cost confrontation, it depends on who invests the most, whether it is talent or money. For me, I would rather trust related cloud services provided by Google, Apple, Microsoft, etc., because I know how strong their security teams are and how large their security investment is. But in addition to fighting against external hacker intrusions, I am also very concerned about the internal security risk control capabilities and the binding force related to privacy data protection. The ones I trust quite well have done a good job of avoiding the security risks I care about. But nothing is absolute. If I choose these clouds to back up my very important data (such as wallet), I will definitely encrypt the wallet at least once again.
I strongly recommend mastering GPG. In addition to the "signature verification" mentioned above, the security of encryption and decryption is also strong enough. For an introduction to GPG, please refer to:
OK, you have mastered GPG:) Now that you have used GPG to encrypt the contents of your wallet (mnemonic phrase or private key) in an offline secure environment, you can throw the encrypted files directly into these cloud services. , save it, it’ll be fine. But here I need to remind you, don’t lose your GPG private key and don’t forget the private key password...
At this point, it seems that the troubles caused by security have not been adapted to. It is not easy to get started with GPG. You have to back up the private key and private key password of GPG. In fact, once you have reached this point and you are familiar with it, it will not be troublesome to back up this little thing. I won’t elaborate on this point, leaving it to you who will gain true knowledge through practice.
If you want to be lazy, there is another option that you can consider, but it will be slightly discounted in terms of security. I can’t measure the specific discount, but sometimes I will be lazy in some scenarios, so I will consider using well-known tools. To assist. This tool is 1Password. The new version of 1Password already supports directly saving wallet-related content, such as mnemonics, passwords, wallet addresses, etc., which is convenient for users. In fact, other tools of the same type (such as Bitwarden) can also be used, but they are not as convenient to use.
Paper, many hardware wallets will come with several good quality paper cards on which you can copy your mnemonic phrase (in clear text, SSS, etc.). In addition to paper ones, there are also steel plate ones (fire-resistant, water-resistant and corrosion-resistant, of course I haven't verified it). After the mnemonic phrase is copied, it will be verified once. If there is no problem, put it in a place you feel is safe, such as a safe. In fact, I personally like Paper. If Paper is in a good environment, its lifespan is much longer than that of electronic equipment.
Device, various devices, electronic devices are commonly used, computers, iPads, iPhones, mobile hard drives, U disks, etc. can be used for backup, depending on personal preference. Then, the secure transmission between devices makes me feel more secure: AirDrop, USB and other point-to-point methods that are very difficult to be hijacked by middlemen. But I am naturally worried about electronic equipment because it may break down after many years, so I will maintain the habit of checking it at least once a year. For some repetitive practices (such as encryption), just refer to the explanations in the Cloud bullet point.
Brain, Memory is very exciting and exciting. In fact, everyone has his own "memory palace". This thing is not mysterious and can be trained. Practice makes perfect and deepens memory. There are indeed many things that are better remembered by the brain. As for whether you should only use the brain to remember things, it depends on yourself. Anyway, be aware of two risks: First, time may cause memory to fade or become confused; second, you may have an accident. Not much to say about this, please expand on your own.
Now you have everything backed up. Don't go too far with the encryption, otherwise it will be like "perish together" after many years, because you may not be able to decrypt it yourself. According to the security rule "continuous verification", no matter whether the encryption and backup methods are excessive or not, verification must be done regularly and irregularly. The frequency of verification depends on your memory. Sometimes you may forget it when you turn around. Verification does not mean that you have to completely unpack it and take a look. As long as the entire process is correct, partial verification is also possible. Finally, attention should also be paid to the confidentiality and security of the verification process.
Okay, let’s take a long breath. In fact, getting started is the hardest part. After you are ready for the above, let’s start to really enter this dark forest:)
Use wallet
The real challenge comes after you create and back up your wallet. Unless you are a very Buddhist person, you don’t play much with the value assets you hold, and you don’t usually play in projects related to smart contracts such as DeFi, NFT, GameFi, etc. of the Ethereum series, or the Web3 that I like to mention at the moment. Then your funds are actually quite safe.
· AML
Well, it's just "pretty safe", because there are still risks here. As the saying goes, "If people sit at home, disaster will come from the sky." Why do you say this way? Think about it, where did your first cryptocurrency come from? Didn't it appear out of thin air? So in the possible cryptocurrency activities, the cryptocurrency you get may encounter AML (Anti Money Laundering), that is, anti-money laundering risk control. In other words, the cryptocurrency you hold at the moment may be unclean, and if you are unlucky enough, it may be frozen directly on the chain. For example, according to public reports, Tether once froze some USDT funds at the request of law enforcement units. . You can see the frozen list here:
To verify whether it is frozen by Tether, you can do it at the USDT contract address:
https://etherscan.io/token/0xdac17f958d2ee523a2206206994597c13d831ec7#readContract
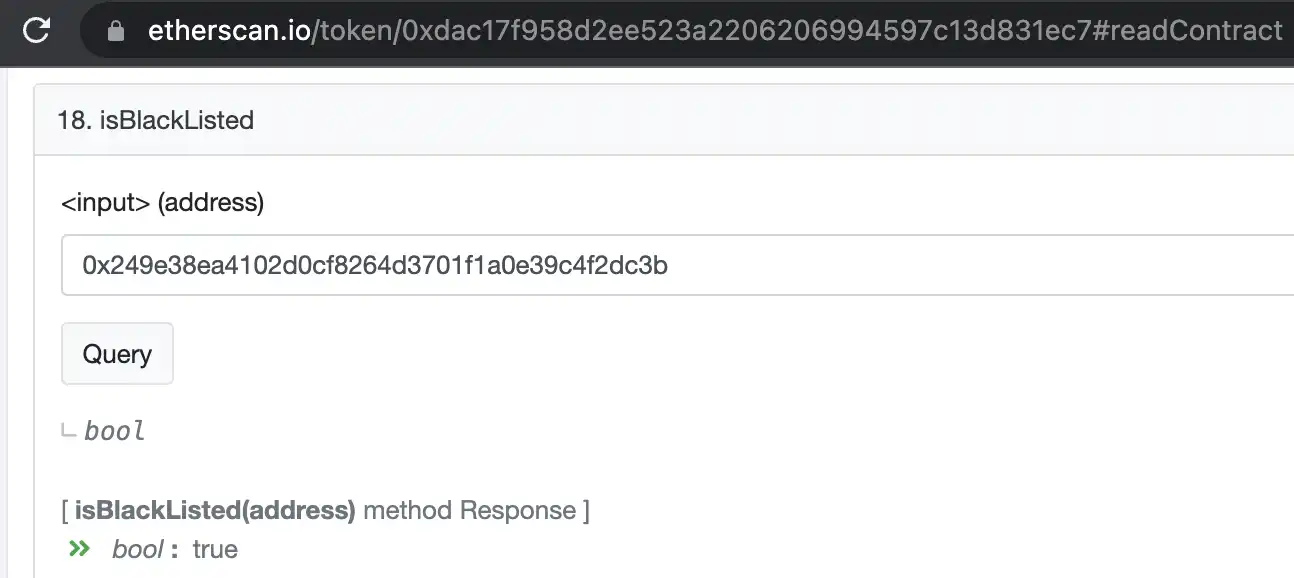
Enter the target wallet address in isBlackListed to determine. The same applies to other chains where USDT is located (don’t take it too seriously).
But your Bitcoin and Ethereum will not be frozen on the chain. Maybe if this happens in the future, then this very firm belief in decentralization may be gone. Most of the cryptocurrency freezes we often hear about now actually do not occur on the chain, but in centralized platforms, such as centralized trading platforms (Binance, Coinbase, etc.). The fact that your cryptocurrency is in these centralized platforms means that you do not actually hold these cryptocurrencies. What the centralized platform freezes is actually your account, especially your trading and currency withdrawal permissions. In fact, the concept of freezing can easily be confusing to outsiders, so some bad self-media has appeared to randomly interpret and spread various conspiracy theories about Bitcoin.
Although your Bitcoin, Ethereum, etc. will not be frozen on the chain, if your cryptocurrencies themselves are involved in cases handled by relevant law enforcement units, once your cryptocurrencies are transferred to a centralized platform, these centralized The platform may freeze your cryptocurrency due to AML and other requirements.
In order to better avoid AML problems, you need to choose a platform or individual with a good reputation as your counterparty. Don't mess around. The basic problem is not big. If you want to solve these problems in depth, there are actually many ways. For example, in the Ethereum series, almost all bad guys and people who are particularly concerned about privacy will choose Tornado Cash for currency mixing. I won’t mention more methods, because these methods can actually be used for evil.
·Cold Wallet
There are several ways to use cold wallets. Since the wallet itself is not connected to the Internet, it can be considered a cold wallet. So how to use it without internet connection? First of all, if you just receive cryptocurrency, it is not a big problem. The experience of using an observation wallet is already quite good. For example, imToken, Trust Wallet, etc. can directly add the wallet address and become the observation wallet of the cold wallet corresponding to the target wallet address.
If the cold wallet wants to send cryptocurrency, there are several common ways:
· QRCode
· USB
·Bluetooth
All of these require special applications (called here: Light App) to be used with cold wallets. This Light App is connected to the Internet, including the observation wallet mentioned earlier. We only need to understand the essential principles to understand these methods. The essence is: in the end, you only need to find a way to broadcast the signed content onto the chain. Let me roughly analyze the process:
· The content to be signed is transferred to the cold wallet by Light App through these methods.
· The signature is completed by the cold wallet with the private key and then transmitted back to the Light App through these methods.
· Light App broadcasts the signed content to the chain.
So whether it is QR code (QRCode), USB, or Bluetooth, the uses are as mentioned above. Of course, different methods will have different details. For example, the QR code information capacity is limited, and it must be split when the signature data is large.
It seems a bit troublesome to use it this way, but once you get used to it, it feels good and even feels safe. However, don’t overestimate your sense of security, because there are still risks here, and many cases have resulted in heavy losses due to these risks. Risk points include:
· The destination address for transferring coins was not strictly checked, resulting in the coins being transferred to other people. People have inertia or laziness. For example, many times when checking a wallet address, it mainly depends on whether the first and last few characters are correct, rather than a complete check. So the bad guy got excited and used a program to find the same addresses at the beginning and end, and then used some tricks to replace your transfer target address with an address he controlled.
Authorization of related currencies to unknown addresses. Generally speaking, authorization is the mechanism of Ethereum series smart contract tokens, that is, the approve function, one parameter is the target address to be authorized, and the other parameter is the quantity. Many people do not understand this mechanism, so they may authorize an unlimited number of tokens to the target address, and the target address has the authority to transfer these tokens. This is the so-called authorized theft of coins. There are other variants of this method, which will not be expanded here.
· Some seemingly unimportant signatures actually hide huge traps. We will not expand on this point yet, but will analyze it later.
· The cold wallet may not show you enough necessary information, causing you to be careless and misjudge.
It all boils down to two points:
· The user interaction security mechanism of what you see is what you sign is missing.
· The user’s relevant knowledge background is missing.
· Hot Wallet
Compared with cold wallets, cold wallets basically have the same risks as hot wallets. In addition, hot wallets have one more risk: the risk of mnemonic phrases (or private keys) being stolen. At this time, hot wallets have to consider more security, such as the security of the operating environment. If the operating environment has related viruses, there is a risk of being stolen. If there are certain loopholes in the hot wallet, the mnemonic phrase can also be stolen directly through the loopholes.
In addition to the regular currency transfer function, if you want to interact with those DApps (DeFi, NFT, GameFi, etc.), you can either access it directly with its own browser, or interact with the DApp opened in the PC browser through the WalletConnect protocol.
Note: The DApp mentioned in this manual by default refers to smart contract projects running on the Ethereum series blockchain.
By default, such an interaction will not result in the mnemonic being stolen, unless there is a problem with the wallet security design itself. Judging from our security audit and security research historical data, there is a risk that the wallet mnemonic phrase will be directly stolen by malicious JavaScript on the target page. But this situation is relatively rare, because it is actually an extremely low-level mistake, and it is unlikely that well-known wallets will make this mistake.
The issue I am most worried about here is actually none of the above. These are all controllable to me (and you can too). The issue I am most concerned about/worry about is: How does each version iteration of a well-known wallet ensure that it will not be Planting malicious code or backdoors? The implication of this question is very clear: I have verified that the current wallet version has no security issues, and I can use it with confidence, but I don’t know how secure the next version will be. After all, it is impossible for me or my security team to have that much time. Put all your energy and effort into verification.
There have been several incidents of currency theft caused by malicious code or backdoors mentioned here, such as CoPay in the past and AToken recently. You can search for specific incidents by yourself.
In this case, there are several main ways to do evil:
· When the wallet is running, the malicious code directly packages and uploads the relevant mnemonic words to the server controlled by the hacker.
· When the wallet is running, when a user initiates a transfer, information such as the target address and amount is secretly replaced in the wallet background, which is difficult for the user to detect.
· Destroy the random number entropy value related to mnemonic phrase generation, making these mnemonic phrases easier to crack.
Safety is something that the ignorant are fearless and the knowledgeable are in awe of. There are many points that are terrifying to think about. So for wallets that contain important assets, my security principle is simple: don’t update them easily, just use them enough.
· What exactly is DeFi security?
When we mention DApp, it may be DeFi, NFT or GameFi, etc. The security of these is mostly the same, but they will have their own special features. Let’s take DeFi as an example to explain first. When we mention DeFi security, what exactly do we mean? Almost everyone in the industry only looks at the smart contract part. It seems that if the smart contract is safe, it will be fine. Far from it.
DeFi security includes at least the following parts:
· Smart contract security
·Blockchain basic security
· Front-end security
· Communication security
· Human safety
· Financial security
· Compliance and security
Smart contract security
Smart contract security is indeed the most important entry point for security audits. For SlowMist’s security audit points for smart contracts, you can refer to:
https://www.slowmist.com/service-smart-contract-security-audit.html
For advanced players, if the security of the smart contract part itself is controllable (whether you can conduct a security audit yourself or understand the security audit report of a professional organization), then the security of other parts does not matter. Controllability is a very different understanding, and some of it depends on the player's strength. For example, players have requirements for the risk of excessive smart contract authority. Unless the project party itself is strong and has a good reputation, complete centralization does not matter. But for those lesser-known, controversial or emerging projects, if you say that the smart contract of this project has the risk of having too much authority, especially if this authority can also affect your principal or income, you will definitely No longer willing.
The risk of excessive authority is very subtle. In many cases, authority is convenient for project parties to do related governance and risk response. But for us, this is a consideration of human nature. What if the project party does evil? So there is a compromise practice in the industry: adding timelock (Timelock) to solve some risks of excessive permissions, such as:
Compound, this well-known old DeFi project, has a Timelock mechanism added to the admin permissions of its core smart contract module Comptroller and Governance:
Comptroller(0x3d9819210a31b4961b30ef54be2aed79b9c9cd3b)
Governance(0xc0da02939e1441f497fd74f78ce7decb17b66529)
The admin address is:
Timelock(0x6d903f6003cca6255d85cca4d3b5e5146dc33925)
You can directly see on the chain that the time lock (delay parameter) of Timelock is 48 hours (172800 seconds):
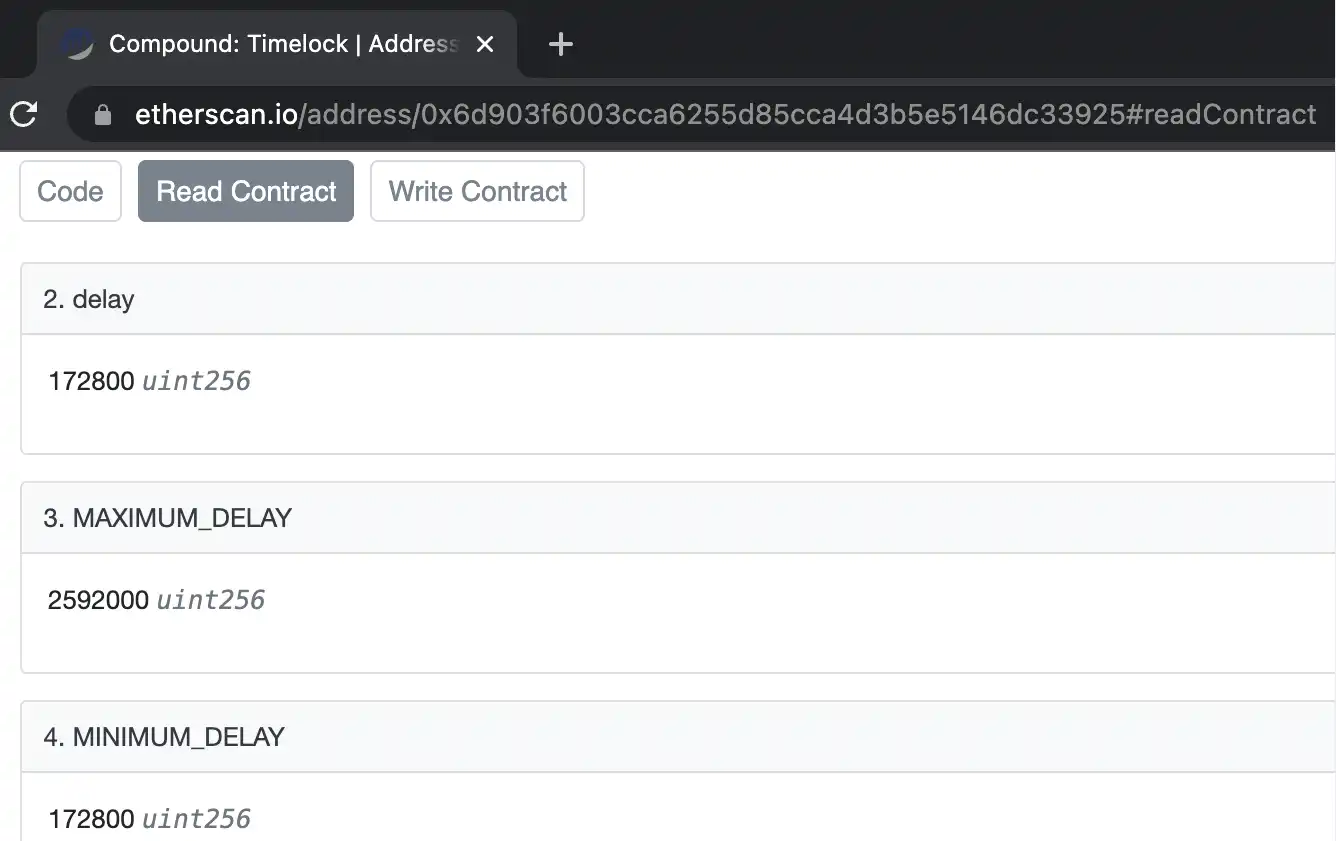
In other words, if Compound's admin (project party) needs to change some key values of the target smart contract, the transaction will be recorded after it is uploaded to the chain, but it must wait 48 hours before the final execution can be completed. This means that if you want, you can audit every operation of the admin, and you have at least 48 hours to respond. For example, if you are worried, you can withdraw your funds within 48 hours.
Another way to reduce the risk of excessive permissions of the project team is to multi-sign the admin, such as using Gnosis Safe for multi-sign management, so that at least there will be no one-note speech. What needs to be noted here is that multiple signatures can be "the emperor's new clothes", for example, one person holds multiple keys. Therefore, the multi-signature strategy of the target project needs to be clearly stated and clearly stated, who will keep the keys, and the role of the key keeper must also be reputable.
Special attention needs to be paid here. Any security strategy may suffer from the "Emperor's New Clothes" problem, which may appear to be good but actually not, presenting a false sense of security. For another example, Timelock seems to be a good thing. In fact, there have been cases where the Timelock deployed by some projects has a backdoor. Users generally don't look at the Timelock source code directly, and they may not understand it, so they put a backdoor there, and no one may notice it for a while.
In addition to the risk of excessive authority, other aspects of smart contract security are also critical, but the threshold for understanding is still quite high, so I won’t go into details here. My suggestion is this: at least you can gradually learn to read security audit reports. Practice makes perfect.
Blockchain basic security
The basic security of blockchain refers to the security of the blockchain itself, such as: consensus ledger security, virtual machine security, etc. If the security of the blockchain itself is worrying, the smart contract projects running on it can also directly suffer from the northwest wind. How important it is to choose a blockchain that is sufficiently secure and well-known, or even one that has a high probability of having a long history.
Front-end security
Front-end security is really a devil. It is too close to users, and it is especially easy for users to be confused and deceived. Maybe everyone’s main attention is on the security of their own wallets and smart contracts of the target project, and front-end security is easily overlooked. Here I need to emphasize again, front-end security is the devil! Let me focus on it.
What I care about most about front-end security is: How do I know that the object I interact with in this front-end page is the smart contract I think it is?
This insecurity is mainly due to the following two risks:
· Internal evil
· Third parties commit evil acts
Internal evil is easy to understand. For example, developers secretly replace the target smart contract address in the front-end page with a backdoor contract address, or directly implant an authorization phishing script. When you visit the front-end page, a series of subsequent operations involving cryptocurrency in your wallet may be completed in a trap. Before anyone knew it, the coin was gone.
Third-party evil mainly refers to two types:
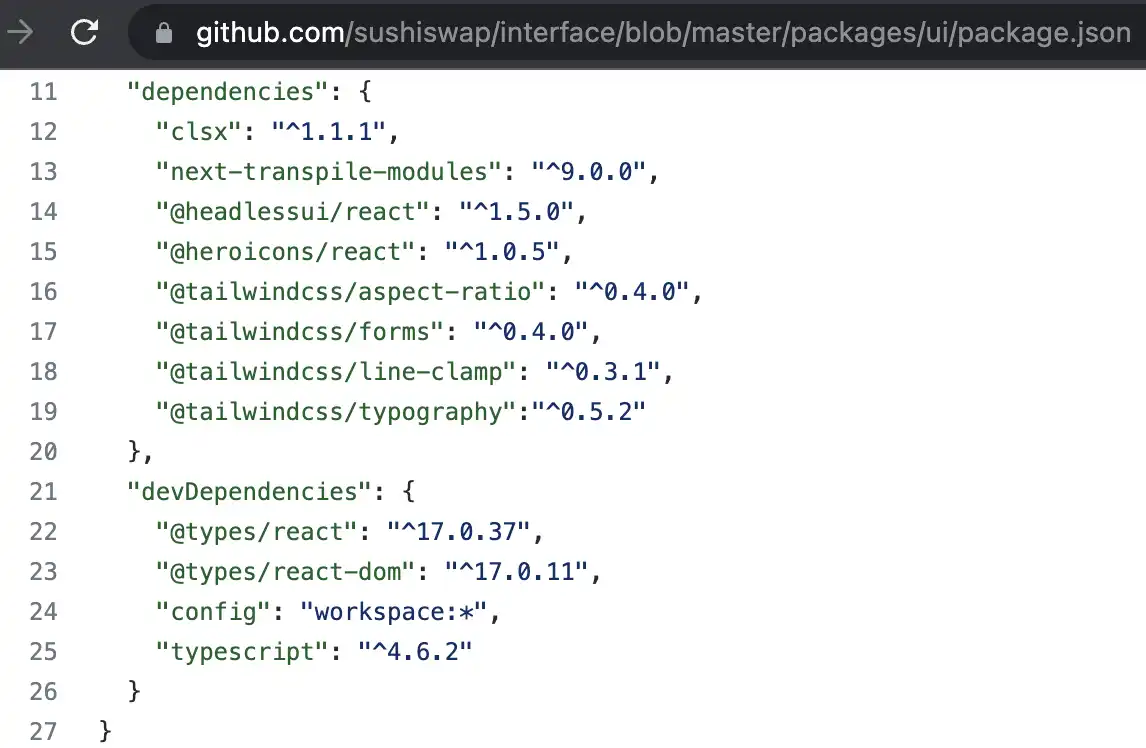
· One is supply chain evil. For example, the third-party module that the front-end relies on is implanted with a backdoor, and is directly brought into the target front-end page along with the packaging and release. Such as SushiSwap (just an example, it does not mean that the project in the screenshot has this problem):
· One is a third-party remote JavaScript file introduced by the front-end page. If this JavaScript file is malicious or hacked, the target front-end page may be affected, such as OpenSea (just an example, it does not mean that this has happened to the project in the screenshot) question):
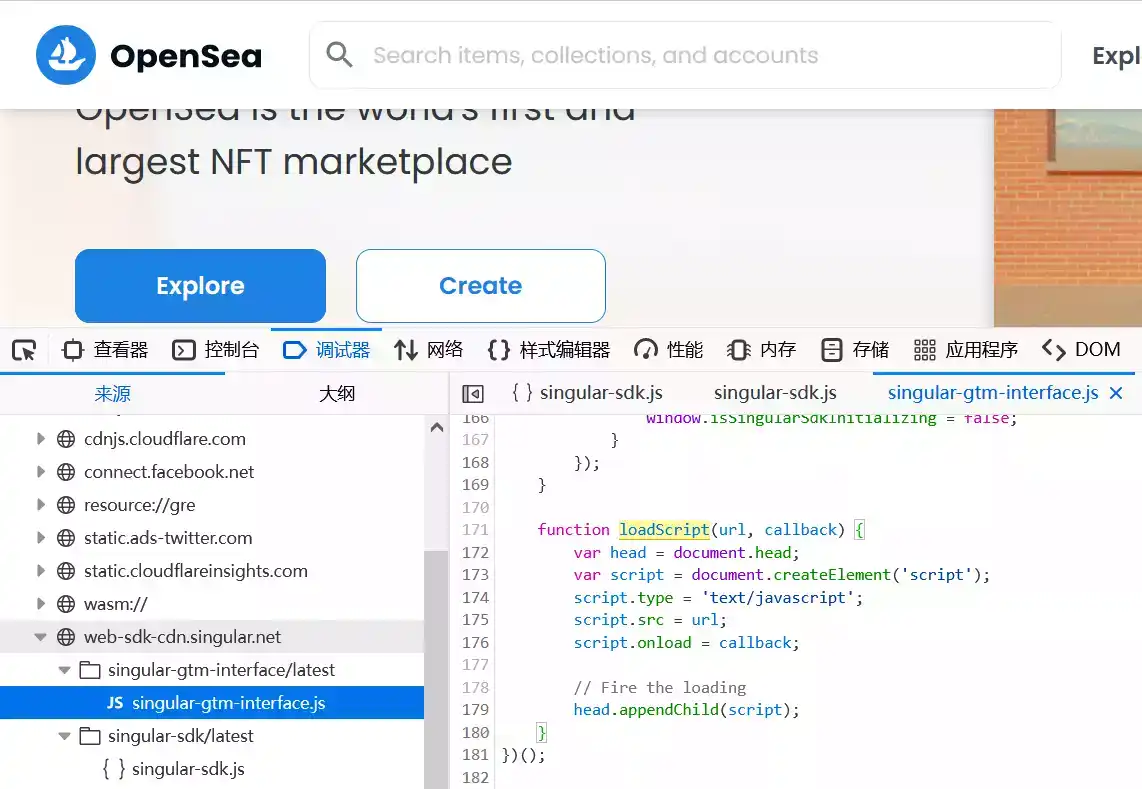
The reason why it is mentioned here that it may be affected is because if the project party references the third-party remote JavaScript file in the following way on the front-end page, it may not be affected:
<script src=”https://image.theblockbeats.info/other/pic404.png”https://example.com/example-framework.js” target=”_blank” rel=”noopener noreferrer”>https://example.com/example-framework.js” integrity=”sha384-Li9vy3DqF8tnTXuiaAJuML3ky+er10rcgNR/VqsVpcw+ThHmYcwiB1pbOxEbzJr7″ ></script>
The key point here is a good security mechanism of HTML5: the integrity attribute (SRI mechanism) in the tag. Integrity supports sha256, sha384, sha512. If the third-party JavaScript resource does not meet the hash integrity check of integrity, it will not Loading, this can prevent unexpected code execution. But using this mechanism requires that the target resource supports CORS response. Specific reference:
https://developer.mozilla.org/zh-CN/docs/Web/Security/Subresource_Integrity
Wait, why did I mention "possible" before? It's because there are scenarios where it can be bypassed. I won't mention the bypass methods, because in most cases, you only need to pay attention to whether the target front-end page has an integrity mechanism when introducing third-party remote JavaScript files. Sadly, OpenSea doesn't, so let's wish it the best.
Communication security
For communication security, focus on HTTPS security. First of all, the target website must be HTTPS, and HTTP clear text transmission is never allowed. Because HTTP plaintext transmission is too easy to be hijacked and attacked by man-in-the-middle, secure transmission protocols such as HTTPS are now very common. If there is a man-in-the-middle hijacking attack on HTTPS, such as implanting malicious JavaScript code into the target front-end page, the browser will inevitably display a highly visible reminder of an HTTPS certificate error. For example, there was the pitfall of MyEtherWallet.
MyEtherWallet used to be a very popular web wallet and is now quite well-known, but it is no longer just a web wallet. I have said before that I strongly do not recommend using web wallets. In addition to various front-end security issues, there may also be the risk of HTTPS hijacking.
On April 24, 2018, MyEtherWallet experienced a major security incident involving HTTPS hijacking. The review shows:
https://www.reddit.com/r/MyEtherWallet/comments/8eloo9/official_statement_regarding_dns_spoofing_of/
https://www.reddit.com/r/ethereum/comments/8ek86t/warning_myetherwalletcom_highjacked_on_google/
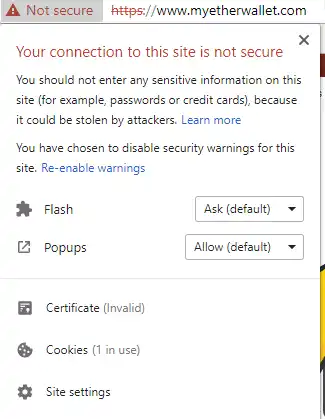
At that time, hackers hijacked the DNS service (Google Public DNS) used by a large number of MyEtherWallet users through BGP, an ancient protocol. This caused many users to have HTTPS error certificate prompts appear in their browsers when accessing MyEtherWallet. In fact, if you encounter an incorrect certificate, in principle, you should not continue to access it, because it means that the target page has been hijacked. However, many users really do not understand this security risk. At most, they hesitate to ignore the error certificate reminder and continue to force access.
Since the target page has been hijacked, the hacker injected malicious JavaScript code, directly stealing the target user's plaintext private key on the target page, and then transferred the cryptocurrencies (mainly ETH) related to these users in batches.
This is definitely a classic case. In order to steal coins, hackers used BGP hijacking, which was really a big mistake. There have been several similar cases since then, so I won’t mention them here. There is actually only one thing that users need to pay attention to here. When you really want to use a web wallet or play related DApps, you must pay attention: when an HTTPS error certificate reminder appears on the target page, immediately stop accessing and close the page. Then Nothing will happen to you.
There is a cruel reality in security, which is this: when risks have arisen, don’t give users a choice. Once given, there will always be users who will fall into the trap for whatever reason. In fact, the project side needs to shoulder relevant responsibilities here. For example, for HTTPS hijacking, there are actually good security solutions. The project side's developers only need to configure HSTS. HSTS, the full name of HTTP Strict Transport Security, is a web security policy supported by browsers. If this configuration is turned on, the browser will forcibly prevent the user from continuing to access after discovering an HTTPS certificate error. Do you understand what it means?
human security
Human security is easy to understand, such as internal evil within the project team. This has been mentioned in some aspects before, so I won’t go into too much detail for the time being. Because later, this section will be discussed specifically.
financial security
Financial security is a concept that requires awe. When it comes to DeFi, users are most concerned about the price of the currency and the annualized return, which must be good or at least stable. In short, as a user, I play this DeFi and I want to make money. If I lose money, I have to be convinced. Well, this is also human nature.
Possible criticisms of this part include:
· Unfair start, such as pre-mining and rat bin.
· Giant whale attack, the so-called money ability.
· Heizhuang, see who can run faster.
· Market black swans, such as sudden waterfalls, and the matryoshka or interoperability between Target DeFi and other DeFi/Tokens. At this time, the shortcomings of the barrel may be determined by other DeFi/Tokens.
· There are also some more technical or scientist techniques, such as front-running, sandwich attacks, flash loan attacks, etc.
Compliance and security
Compliance security is a very big topic, and the aforementioned AML (Anti Money Laundering) is just one of them, as well as KYC (Know Your Customer), sanctions area restrictions, securities risk-related content, etc. In fact, for users, these are not something we can fight against. We can only say that when playing a project, the target project may be subject to security supervision in some countries, so there may be issues with the collection of privacy information that we care about. You may not care about this privacy, but there are people who do.
For example, a small thing appeared in early 2022: the wallet supports the Address Ownership Proof Protocol (AOPP) protocol.
At that time, I looked at the protocol design of AOPP and found that wallets that support AOPP may leak user privacy: regulatory agencies will have the ability to know the relationship between a regulated trading platform and an unknown external wallet. refer to:
No wonder many privacy wallets took this feedback seriously and removed support for this protocol. Having said that: this protocol design is really interesting. I noticed that some wallets have no plans to remove support for AOPP, such as EdgeWallet. Their view is that AOPP does not expose more user privacy and can provide greater help for the circulation of cryptocurrency, because if users cannot If you prove that an external wallet address belongs to you, some regulated trading platforms will not allow users to withdraw coins to this external wallet address.
At first, the well-known hardware wallet Trezor did not delete the support for AOPP. Later, it compromised and deleted it under pressure from the community and users on Twitter.
You see, such a small thing is actually a big privacy matter for some people. This does not mean fighting against regulation, regardless of compliance and safety. In fact, in my opinion, appropriate compliance and security compromises are necessary. I won’t expand on this topic further, just understand it according to your comfortable way.
At this point, the relevant content of the main parts of DeFi security has been introduced.
In addition to the above, there are also security issues introduced by future additions or changes. We often say "security is dynamic, not static", and this is what we mean. For example, many project parties now have security audits and beautiful security audit reports, but if you carefully read the reports with good quality, you will find that these reports will clearly explain what content was audited in what time frame, and what is the unique mark of the content ( For example, the address after verification of open source on the chain or the commit address of the GitHub warehouse, or the hash value of the target code file). Therefore, the report is static. If you find that the target project does not conform to the description in the report, you can point it out.
· NFT security
Almost all the DeFi security mentioned earlier can be applied to NFT security, but NFT has its own unique security points, such as:
· Metadata security
· Signature security
Metadata mainly refers to pictures, animations and other content. For specific standard recommendations on Metadata, please refer to OpenSea:
There are two main security issues that may arise here:
· One is that the URI where the picture (or animated picture) is located is not trustworthy. For example, a random centralized service is unstable on the one hand, and on the other hand, the project party can change the picture at will, so the digital collection capability of NFT will be gone. . Generally, decentralized storage such as IPFS and Arweave are used, and well-known URI gateway services are used.
· Another problem is that it may cause privacy leakage. Random URI can collect the user's basic privacy (such as IP, User-Agent, etc.).
Signature security issues are serious and will be discussed below.
· Be careful with your signature!
Signature security is something I particularly need to mention, because there are many pitfalls in signature protocols, and several security incidents have occurred, especially around NFTs. But I noticed that too many people are still unable to deal with this part of the security issue well. The reason is that few people explain this part of the security issue clearly.
The first and greatest security principle to abide by in signature security is: what you see is what you sign. That is, the content you see is what you expected to sign. When your signature is sent, the result should be what you expected, and it will never be a slap in the face afterwards.
Some contents related to signature security are mentioned in the "Cold Wallet" section. If you are not impressed, I suggest you review it. Here we focus on different contents.
OpenSea has experienced several theft incidents of well-known NFTs held by users around 2022, especially the concentrated outbreak on 2022.2.20. The fundamental reasons are:
· The user has authorized the NFT (pending order) in OpenSea.
· Hackers use phishing to obtain relevant signatures of users.
A more correct interpretation can be found here:
It is not difficult to obtain this relevant signature. The hacker needs to construct the correct content to be signed, hash it, and trick the target user into completing the signature (this is a blind signature, which means that the user actually does not know what the content of his signature is) , the hacker gets the signed content, organizes the application data, and completes the application.
Let me use one of the NFT markets to explain specifically (not necessarily OpenSea). When the target user authorizes the relevant NFT order in the NFT market, the attacker constructs the correct content to be signed, and after hashing it with Keccak256, pops up the content to be signed on the phishing page to the user. What the user sees at this time as follows:
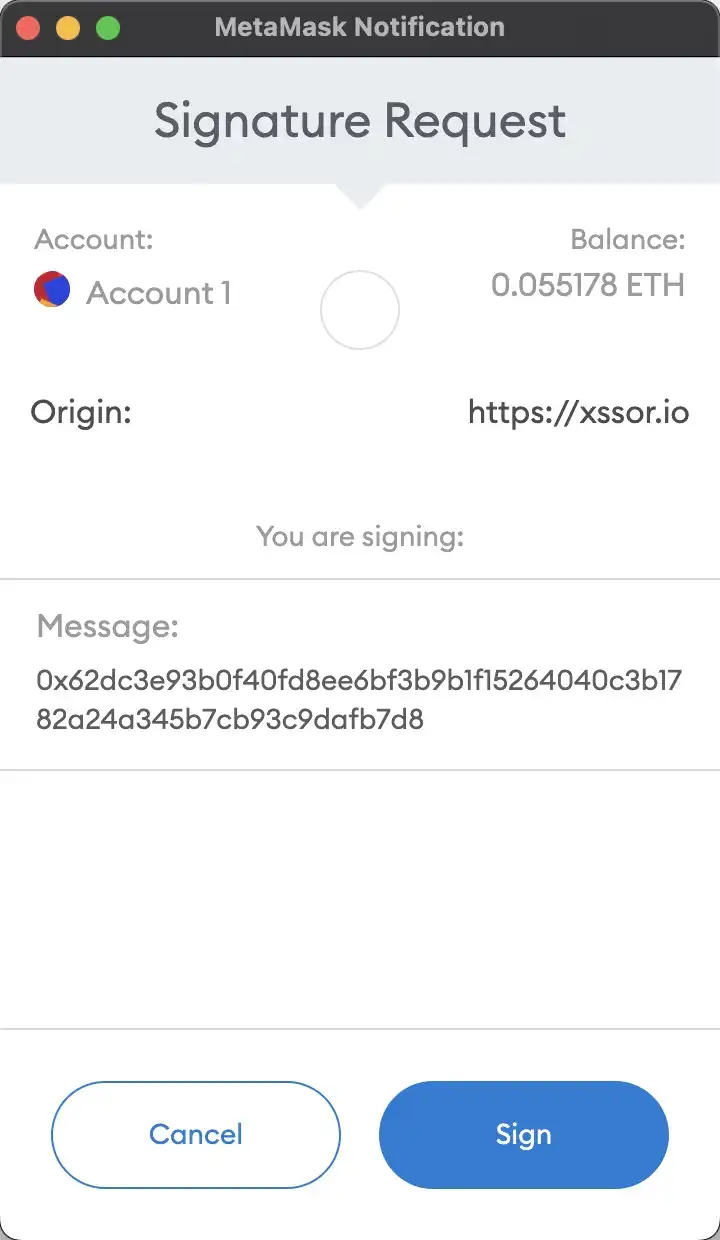
Look carefully, what can you see in the window that MetaMask pops up? The account and balance, the source website of the signature request, and the message being signed are gone... With this content, how could the user think that once they click "Sign", disaster will strike and their related NFTs can be stolen. .
This is actually a kind of blind signature. Users do not need to sign in the NFT market and can be tricked into signing on any website (phishing website). The user does not know the actual meaning of these signatures at all. Unfortunately, hackers do. For users, just remember: refuse blind signing. OpenSea had a blind signing situation before, but it was improved after 2022.2.20, and it was upgraded and improved using EIP-712. But even if it is not blind signing, there are still users who will be careless.
The most essential reason why this happens is that the signature is not constrained by the browser's same-origin policy. You can simply understand it as: the same-origin policy can ensure that a behavior only occurs under a clear domain name and does not cross borders. Occurs across domains, unless the project party intentionally wants it to occur across domains. If the signature has a same-origin policy, then the request signature generated by a non-target domain name, even if the user signature is completed, the hacker cannot use this signature for attacks under the target domain name. I won’t continue to talk about the protocol-level security improvements. I have noticed the new draft and I hope this situation can be improved as soon as possible.
The signature security mentioned so far covers the main methods, but there are actually many variations. In any case, they remain the same. The best way to understand it thoroughly is to reproduce the attack from beginning to end yourself, or even create some unique attack methods. For example, the signature mentioned here actually contains a lot of details, such as how to construct the content to be signed and what is the specific content after signing? In addition to approve, are there any other authorization methods (yes, such as increaseAllowance). Well, it would be too technical to expand here. It’s good that you understand the importance of signatures.
For users, it is possible to combat this type of attack at the source by deauthorizing (approve). You can use the following well-known tools to operate:
· Token Approvals
It is an authorization check and cancellation tool provided by the official browser of Ethereum. The Ethereum series of blockchains are basically similar, because their blockchain browsers are basically developed by Etherscan, such as:
· Revoke.cash
Old classic, only supports Ethereum.
· APPROVED.zone
It is also an old brand and only supports Ethereum.
· Rabby extension wallet
We have a lot of security cooperation with this wallet. Their "authorization check and cancellation" function supports the most Ethereum series I have ever seen...
· Be careful with signatures that go against common sense!
It’s not over yet, I want to mention one more risk:Counter-common sense risk.
What is counter-intuitive? For example, if you are already very familiar with Ethereum, novices in various DeFi and NFT games will call you boss. At this time, you went to play Solana and also encountered various phishing websites. You were not afraid and smiled scornfully: "These are all useless in the Ethereum series ecosystem. How could I be fooled?"
Sorry, the hacker laughed, you were indeed fooled. Because there is a counter-intuitive process, people have inertia or laziness, which causes you to be careless and not dodge.
Okay, let’s take a look at this real-life case that defies common sense.
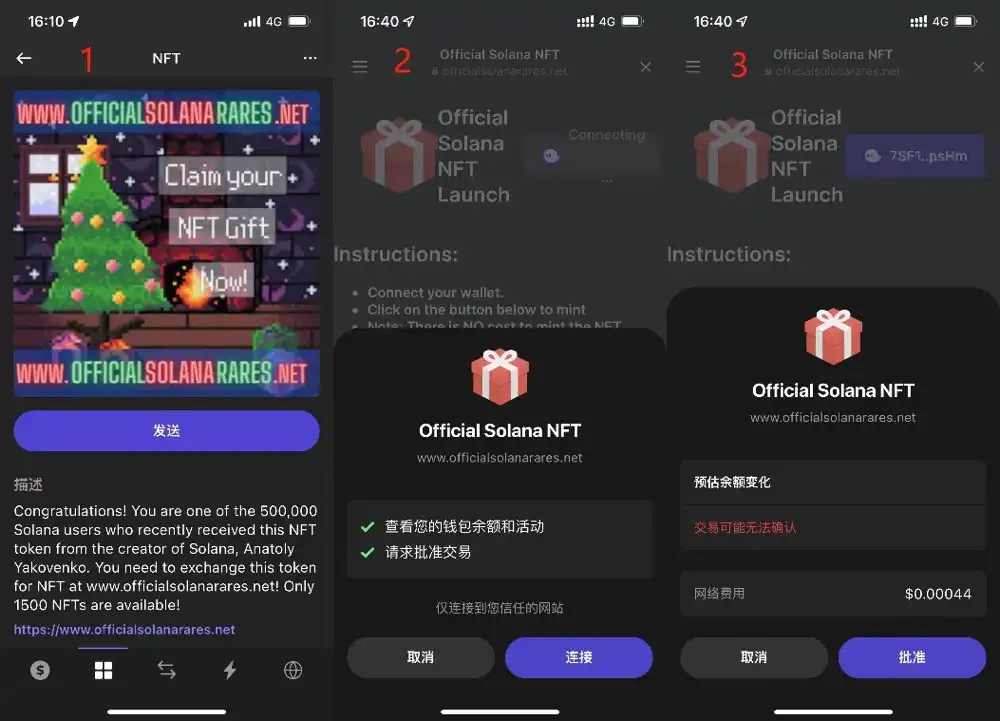
2022.3.5, a security warning: Authorization phishing on Solana is much more cruel. Attackers airdrop NFTs to users in batches (Figure 1). Users enter the target website through the link (www_officialsolanaares_net) in the airdrop NFT description content and connect to the wallet (Figure 2 ), click "Mint" on the page, and the approval prompt box appears (Figure 3). Note that there is no special prompt in the approval prompt box at this time. Once approved, all SOL in the wallet will be transferred.
When clicking "Approve", the user will interact with the malicious contract deployed by the attacker: 3VtjHnDuDD1QreJiYNziDsdkeALMT6b2F9j3AXdL4q8v
The ultimate function of this malicious contract is to initiate a "SOL Transfer" and transfer almost all of the user's SOL. Judging from the information on the chain, the phishing behavior has been going on for several days, and the number of victims is increasing.
There are two pitfalls here that you need to pay attention to:
1. After the user approves (Approve), the malicious contract can transfer the user's native assets (here, SOL). This is impossible on Ethereum. Ethereum's authorized phishing cannot take away Ethereum's native assets ( ETH), but the tokens on it can be fished away. So there is a "violation of common sense" phenomenon here, which makes users easy to take it lightly.
2. Solana’s most well-known wallet, Phantom, has flaws in the “What you see is what you sign” security mechanism (other wallets have not been tested) and does not give users complete risk reminders. This can easily create security blind spots and cause users to lose coins.
· Some advanced attack methods
There are actually many advanced attack methods, and most of them from the public perspective are just: I was phished. But this fishing is really advanced, such as:
The hacker sends the phishing via email, and the document attached to the email is:
A Huge Risk of Stablecoin(Protected).docx
This is indeed an attractive document... but once this document is opened, a Trojan horse may be implanted in the computer (usually through Office macro scripts or 0day/1day). Such Trojan horses generally include the following general functions:
· Collection of various credentials, such as browser, SSH related, etc., so that hackers can extend their tentacles to other services of the target user. Therefore, after being poisoned, users are generally advised not only to clean the target device, but also to change the relevant account permissions in a timely manner.
· Keyboard logging, especially collecting sensitive content that appears temporarily, such as passwords, etc.
· Relevant screenshots, collection of sensitive documents, etc.
· If it is a ransomware virus, the further step is to highly encrypt the files on the target device and wait for the victim to pay the ransom, usually in Bitcoin. But this is not a ransomware virus. After all, the actions of the ransomware virus are too big and the intention is direct and crude.
In addition, Trojans targeting the cryptocurrency industry will also be specially customized for use, such as collecting sensitive information from well-known wallets and trading platforms to steal coins. For the Trojan mentioned above, professional analysis can reveal that there is a special attack against MetaMask:
https://securelist.com/the-bluenoroff-cryptocurrency-hunt-is-still-on/105488/
The Trojan will replace the user's MetaMask with a backdoored MetaMask. A backdoored MetaMask means that the cryptocurrency you use in it is no longer yours. Even if you are equipped with a hardware wallet, this MetaMask with a backdoor will steal coins by tampering with the target address and amount.
This type of attack is specifically targeted at high-profile individuals with exposed wealth. What I have noticed is that some famous people are too arrogant, and it is only a matter of time before they are hacked. Generally, after being hacked, many people will learn from the lessons, conduct a comprehensive review, make comprehensive improvements, and maintain long-term cooperation and friendship with trustworthy professional security people or organizations. However, there are always exceptions in this world. Some people or projects are hacked once, and they will be hacked a second or third time. If it is said that heaven will give great responsibility to people, and every time they are hacked, they really meet their opponents, then I will respect this person or the project side very much, and call it a pioneer, and there is a high probability that it will develop in the future. . Unfortunately, many hacks are caused by low-level problems, and one can draw inferences about other cases. This is really incomprehensible. It is recommended to stay away from such people or project parties.
The phishing attack that casts a wide net is actually a general technique. It is nothing more than preparing a batch of phishing websites with similar domain names and buying accounts on social platforms such as Twitter to spread them. If you know the hot spots and techniques well, you will get a lot of scams. This kind of phishing is nothing special. It usually involves roughly authorizing the user's wallet to authorize related tokens (including NFT) and then stealing them.
There are also some advanced attacks, such as combining XSS, CSRF, Reverse Proxy and other techniques to make the entire attack smoother. We can’t talk about everything, but here we can talk about one of the very detailed exploit points (Cloudflare man-in-the-middle attack), which belongs to the scenario related to Reverse Proxy. This exploit point has already had a real currency theft attack, and it is very hidden.
The problem here is not that Cloudflare itself did evil or was hacked, but that the project team used Cloudflare and the project team's account permissions were stolen. The general process is like this. If your website uses the Cloudflare service, you can notice the Workers function module in the management background. The official statement of this Workers is:
Build serverless applications and instantly deploy them globally for superior performance, reliability, and scale. Specific reference:
I made a test page very early:
There will be a pop-up window after you visit, the content is:
xssor.io, Hijacked by Cloudflare.
In fact, this pop-up window and even the entire x.html content do not belong to the file itself, but are all provided by Cloudflare. The principle is shown in the figure below:
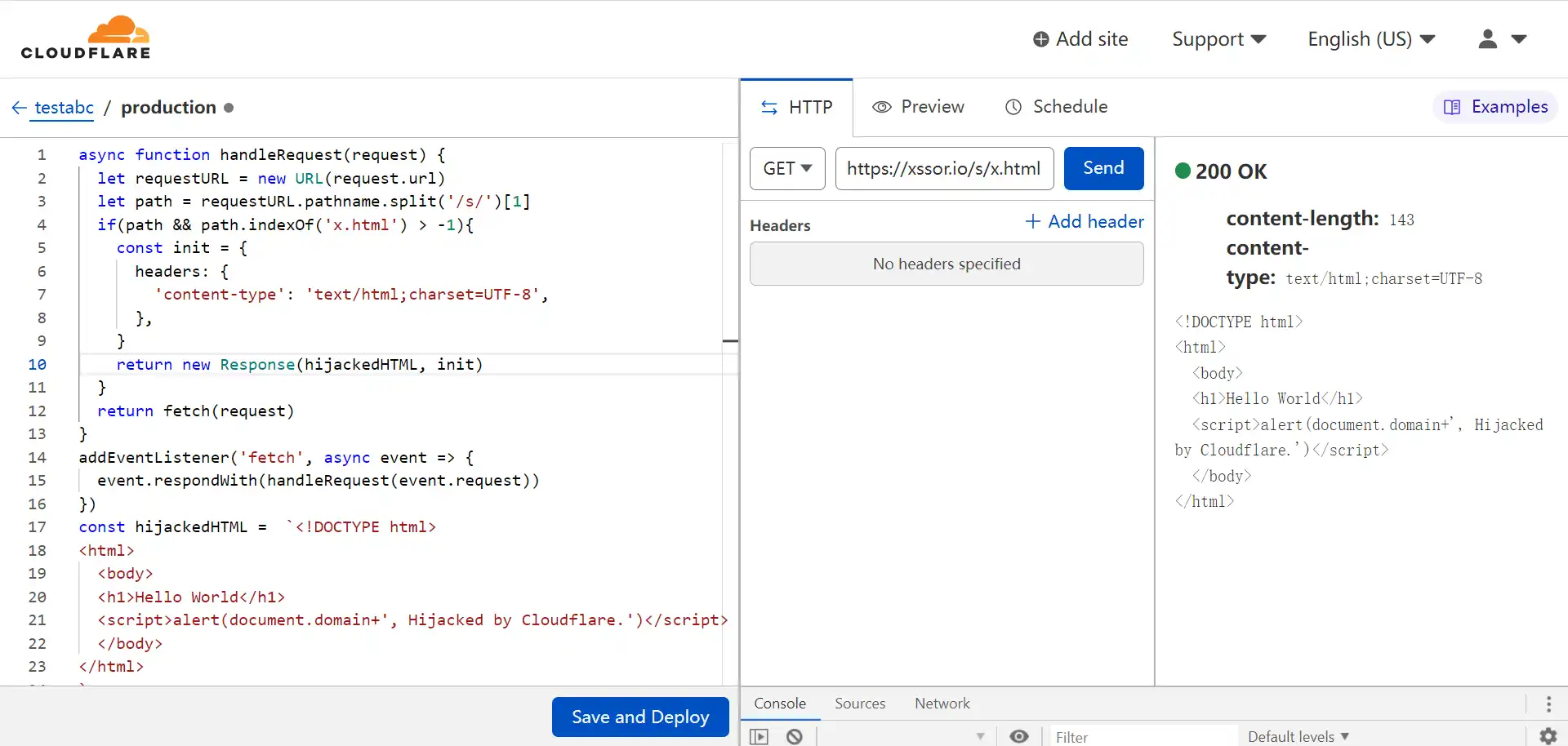
The meaning of the code in the screenshot is very simple: if I am a hacker and I control your Cloudflare account, I can use the Workers feature to inject any malicious script into any page. But at this time, it is difficult for users to realize that the target page has been secretly hijacked and tampered with in this way. The target page will not have any error prompts (such as HTTPS certificate errors), and even the project team will not realize that there is a problem for a while. A lot of time was spent checking the security of servers, personnel, etc. Once you realize this, the losses will be huge.
Cloudflare is actually very good. Many websites or web services use Cloudflare for web firewalls, combating DDoS attacks, global CDN acceleration, reverse proxy and other scenarios. Since there is a free version, there are many users, similar to Cloudflare, there are also services such as Akamai .
Users must pay attention to the security of their own accounts of this type. The issue of account security has been discussed all over the world since the Internet became popular, and it seems that it will explode again. But there is no way, too many people will be hacked because of their account security. For example, passwords for important services are not the only strong passwords used (the popularity of password security management software such as 1Password is actually very worrying). Another example is two-factor (2FA), which is too lazy to turn on, doesn’t even know it exists, and doesn’t know how to do it. use. Not to mention that for some services, passwords must be reset at least once a year.
Okay, let’s introduce some advanced attack techniques first. For you, just understand that this is indeed a dark forest, and learn more about the various attack methods whenever possible. After seeing more, and even stepping on a few pitfalls yourself, you can at least become a non-professional network security personnel (such an identity is great, and many skills are not burdensome).
Traditional privacy protection
It’s not easy, you’ve learned this far. Traditional privacy protection is a cliché. I wrote an article in 2014:
Privacy explodes, you have to learn a few tricks to protect yourself
Looking back at this article, most of the suggestions are not outdated. I suggest you digest them quickly. After all, this article was a very entry-level article. Now I will start a new introduction. Privacy protection is actually closely related to security. You can also think of it as your security protection. What is it protected? Of course it is your privacy, private keys and so on are a type of privacy. In addition, don’t ignore tradition because it is the cornerstone. The cornerstone is no longer safe, the privacy of the cornerstone is gone, and the superstructure is just a castle in the air, precarious and fragile.
Here are two resources that I highly recommend:
one is:
SURVEILLANCE SELF-DEFENSE
TIPS, TOOLS AND HOW-TOS FOR SAFER ONLINE COMMUNICATIONS
SSD (SURVEILLANCE SELF-DEFENSE), or Surveillance Self-Defense, was initiated by the very well-known Electronic Frontier Foundation (EFF). It has specially produced relevant guides to tell you how to avoid Big Brother (Big Brother) in the horizontal Internet world of surveillance/surveillance. Brother) looks at you. It includes many useful tools (such as Tor, WhatsApp, Signal, PGP, etc.).
the other is:
Privacy Guide: Fight Surveillance with Encryption and Privacy Tools
This website is dedicated to listing related tools, and it is very comprehensive. did you see it? It also recommends cryptocurrency trading platforms, wallets, and more. Note that I actually don’t use many of the tools listed on the website. The main reason is that I have my own way. You should gradually form your own way and constantly compare and improve.
Here I will focus on the tools that I think you must master or use no matter what.
· operating system
The security of Windows 10 (and above) and macOS is quite satisfactory, whichever you choose is fine. If you can control it well, you are free to use Linux, such as Ubuntu, or operating systems with perverted privacy and security such as Tails and Whonix.
The easiest security principle for operating systems is to pay attention to system security updates and act immediately when security updates are available. Then there is the mastery of some driving skills. Many people say what other driving skills need to be learned for Windows and Mac computers? Wouldn't it be enough to just click here and there? Of course not. For security novices, installing anti-virus software is an absolute standard, such as Kaspersky and BitDefender, which have good reputations and are also available on Mac.
Then remember the safety principles for downloading, which were mentioned earlier. Not messing with the process has actually eliminated most of the risks.
Then you can think about it, what should you do if your computer is lost or stolen? A computer power-on password is not enough. If the disk is not encrypted, bad guys can just remove the disk and take away the data inside. At this time, I recommend setting up disk encryption protection for important computers. refer to:
https://docs.microsoft.com/zh-cn/windows/security/encryption-data-protection
There is also VeraCrypt, a disk encryption artifact that used to be TrueCrypt, which is very legendary and very powerful. If you are interested, you can learn about and adapt to:
A further step would be to enable a BIOS or firmware password, it's up to you, but that's what I did anyway. But be sure to remember the relevant password, otherwise the gods may not be able to save you. I am honored to have stepped into this pit. Now that I think about it, I wasted a laptop, a little cryptocurrency, and a week of time, but I have accumulated valuable experience in stepping into this pit.
· cell phone
The main mobile phones are iPhone and Android series, which are no longer available. For example, my favorite Blackberry has been eliminated by the times. The security of Android was very worrying in the past. On the one hand, it was in the early stage of development, and on the other hand, there were too many fragmented versions. Different mobile phone brands had their own fork versions. Now security is getting much better.
For mobile phones, we should also pay attention to the safety principles of system security updates and downloads, and be wary of the following points:
· Do not jailbreak or root crack, unless you are doing security research, otherwise it is not necessary. If you are doing this for pirated software, whether it is good or not depends on your control ability.
· Don’t download apps from unofficial markets, again, unless you can control it. And even if you download the App from the official market, there are many fake ones, so be careful to identify them.
· The prerequisite for using the official cloud synchronization is: you are sure that there is no problem with the account security, otherwise the cloud will be controlled and the mobile phone will be in trouble.
In terms of mobile phones, I personally rely more on iPhone. At the same time, prepare at least two iCloud accounts, one in China and one overseas, and install apps with different regional restrictions (very strange, but this is reality).
· network
Network security issues used to be terrible, but they have gradually improved in recent years, especially after the HTTPS Everywhere policy became popular. If a network hijacking (man-in-the-middle attack) does occur, the system will provide corresponding error feedback. But there are always exceptions, so when it comes to the Internet, if you can have a safe choice, of course choose a safe one. For example, do not connect to unfamiliar Wi-Fi randomly, especially when 4G/5G, a highly secure network, is so popular, unless the signal is poor and you are in a hurry to use it.
If you are a security freak, you may want to consider a separate network for your very important and sensitive devices. Choose a router and operator with a good reputation, don't be greedy for small gains, and pray that there will be no advanced evil behavior at the router or operator level.
· Browser
The most popular browsers are Chrome and Firefox. There are also people in the cryptocurrency industry who use Brave, which is fine. Those with high visibility and strong teams will have more timely security updates. The topic of browser security is too broad. For you, you only need to pay attention to the following points:
· Update as soon as there is an update, don’t leave it to chance.
· Do not install extensions if they are not necessary. When installing, you must also pay attention to word of mouth, user scale, and which well-known company maintains the extension. Be careful about the permissions applied for extensions. Extensions must come from the browser's own app store.
· Multiple browsers can coexist. It is strongly recommended that important operations be performed in one browser, while other regular, unimportant operations can be performed in another browser.
· Some well-known extensions for privacy protection (such as uBlock Origin, HTTPS Everywhere, ClearURLs, etc.), depending on your personal preference.
I will also use NoScript, an ancient extension artifact, on Firefox. NoScript can very well combat the evil behavior of JavaScript, and it was a powerful tool in the past. Today's browsers are becoming more and more secure, with origin security policy, CSP security policy, cookie security policy, HTTP security response header policy, extended security policy, etc. The current security level of browsers is indeed very different. The space for security extensions like NoScript to be used is getting smaller and smaller. Those who are interested can learn about it on their own.
· Password manager
If you haven't used a password manager yet, either you don't know the security pleasure of using it, or you have your own powerful memory palace. As mentioned before, the risks of brain memory are: first, time may cause memory to fade or become confused; second, you may have an accident. In any case, I still recommend you to use a password manager to match your brain memory, well-known ones such as: 1Password, Bitwarden, etc.
I don’t need to explain this part too much. There are so many related tutorials that it’s easy to get started without even needing a tutorial. What I need to remind you is:
· Never forget your master password, and don’t have the account information related to the master password stolen, otherwise you will be in trouble.
· Make sure your email is secure. If your email is stolen, although this will not expose the sensitive content in your password manager, the bad guys will be able to destroy it.
· I have verified the security of the tools I mentioned (such as 1Password) and have been paying attention to their security incidents, word-of-mouth, dynamics, etc. I cannot ensure that these tools have an absolutely high degree of security, especially cannot ensure that There will be no black swan events in the future.
There is one thing I really appreciate, such as the introduction and instructions on 1Password’s security page:
These include security design concepts, authoritative certifications related to privacy and security, security design white papers, security audit reports, etc. The transparent disclosure of these contents also facilitates necessary verification within the industry. This is very worthy of learning from project parties.
Bitwarden is more thorough. It is fully open source, including the server, and anyone can verify, audit, and contribute.
Did you realize that? 1Password and Bitwarden’s intentions are clear:
I am very safe and care about privacy. Not only do I say it myself, but third-party authorities also say it. You can also verify it. In order to facilitate your verification, I have spent a lot of energy to make everything transparent. It's easy for you to challenge me if I don't do what I say.
What is this called? This is called safety and confidence :)
· Two-factor authentication
The first level of your identity security on the Internet relies on passwords, the second level relies on two factors, and the third level relies on the risk control capabilities of the target project itself. I can’t say that two-factor is standard. For example, the decentralized wallet you are using is annoying enough to have a layer of passwords (now basically equipped with biometrics such as face and fingerprint to improve the experience), forget about two-factor. . But in a centralized platform, there is no need to have two factors. Because anyone can access or have the ability to access the centralized platform, if your password is stolen, it means that your account permissions are lost and your funds are gone. As for your decentralized wallet, the password is only a local authentication. Even if a hacker gets the password, he still needs to be able to access the device where your wallet is located.
Do you understand the difference? Well, well-known two-factor authentication (2FA) tools include: Google Authenticator, Microsoft Authenticator, etc. Of course, if you use a password manager (such as 1Password), it also comes with the 2FA function, which is very convenient. Remember to make a backup no matter what, because losing 2FA is a hassle.
In addition, two-factor authentication can also be a broad concept. For example, when logging in to the target platform with an account and password, our account is usually an email or mobile phone number. At this time, the email or mobile phone number performs the second step of authentication by receiving the verification code, so this can also be considered a two-factor authentication method. However, the security of this method is not that good. For example, if the email is hacked or the SIM card of the mobile phone is hijacked, or the third-party service for sending emails and text messages is hacked, then the verification code sent by the platform will also be visible. Nothing left.
· Scientific Internet
This is for policy reasons, so I won’t go into details. I’ll just compare a few well-known ones. If you have the ability, you must build it yourself, so it is safe and controllable. After all, our starting point is really to surf the Internet scientifically and safely.
If it is not self-built, there is no guarantee that man-in-the-middle attacks will not occur. As mentioned before, the current network environment is indeed not as bad as before, especially after the HTTPS Everywhere policy has become popular. But some calmness may just be the surface of the water. There are already undercurrents under the water but it is not easy to detect. So I don’t have particularly good safety advice in this area. There are thresholds for self-built, but it’s worth it. If it’s really not possible, you must confirm with multiple parties and choose a brand that has been around for a long time and has a good reputation.
Email is a really important basic identity on the Web. We use email to register for a lot of services. Almost all of the email we use is free. It seems like air. You think it will never disappear. What if one day it disappears? Then it would be embarrassing for a lot of services that rely on this mailbox. It is true that such extreme situations will never happen, such as because of wars, natural disasters, etc. Of course, if these extreme situations occur, other than survival will not be so important to you.
In terms of email, you must choose the giants, such as Gmail, Outlook, QQ email, etc. It just so happens that my previous security research direction included this part. For you, the security of these mailboxes is sufficient. But at any time you must be careful about phishing attacks in your mailbox. Not every email needs to be addressed, especially the links and attachment files given in the email. Viruses and Trojans may be hidden in them.
If you encounter an advanced attack on your mailbox, you're in luck.
In addition to the mailbox services of these giants, if you care about privacy, you can learn about two privacy mailboxes with good reputations: ProtonMail and Tutanota. My suggestion is to use the private mailbox to isolate and register services that require special attention to privacy, and pay attention to the frequency of activity. If you are inactive for a long time, the free mailbox may be recycled.
· SIM card
SIM cards and mobile phone numbers are often as important as basic identities like email addresses. In recent years, several major operators in our country have done a good job in protecting the security of mobile phone numbers. For example, there are strict security authentication procedures for canceling and re-issuing SIM cards, which all happen in the business hall. Regarding SIM card attacks, let me give you an example:
In 2019.5, someone's Coinbase account suffered a SIM Port Attack (SIM card transfer attack) and lost more than 100,000 US dollars in cryptocurrency, which was very painful. The attack process is roughly:
The attacker obtained the target user's privacy through social engineering and other techniques, and deceived the operator to obtain a new SIM card, and then easily obtained the target user's permissions on Coinbase through the same mobile phone number. SIMs have all been transferred, which is very troublesome. Basically, many of our online services use secondary verification or direct identity verification through mobile phone numbers. This is a very centralized authentication method, and mobile phone numbers become vulnerable to attacks. weakness.
For detailed analysis, please refer to:
The defense suggestion in this area is actually simple, enable well-known 2FA tools.
Another risk with the SIM card is that if the phone is lost or stolen, it will be embarrassing to take out the SIM card and use it. What I do is for your reference: I have a password (PIN code) set on my SIM card, and I need to enter the correct password every time I turn on the phone or reuse the SIM card. Please inquire yourself for specific strategies. I only remind you: Don’t forget this password, otherwise it will cause trouble and delay things.
· GPG
Many knowledge points in this part have been mentioned in the previous article, but here is a small concept to facilitate future understanding:
Sometimes you will encounter PGP, OpenPGP and GPG, which look similar names. Let’s simply distinguish them like this:
· PGP is the abbreviation of Pretty Good Privacy. It is a commercial encryption software that has been released for more than 30 years and is now owned by Symantec.
· OpenPGP is an encryption standard derived from PGP.
· GPG, full name GnuPG, is an open source encryption software based on the OpenPGP standard.
These bottom layers are similar, and you can use GPG to be compatible with the others. Here again, I strongly recommend: Don’t mess with so many things. In terms of security encryption, making good use of GPG can definitely greatly improve your sense of security!
· Isolation environment
Specifically emphasizing the security principle of isolation environment, the essence is to have zero trust security law thinking. You must believe: No matter how powerful we are, it will be a matter of time before we are hacked, whether by outsiders, insiders or ourselves. When getting hacked, cutting your losses is the first step. The ability to stop losses is ignored by many people, so they may be hacked one after another because of one hack. The essence is that many safety designs do not exist, especially the seemingly crude safety principle of isolation.
A good isolation habit means that when hacked, only the privacy of the hacked target will be lost, without endangering other privacy. for example:
· If your password security habits are good, if one of your accounts is hacked, the same password will not compromise other accounts.
· If your password is not just under one mnemonic phrase, you will not reset it to zero if something goes wrong.
· Your computer is infected with viruses. Fortunately, this is a computer that is specially used for surfing. There is not much privacy in it, so you won’t panic. Reinstallation can solve most problems. If you are good at using virtual machines, even better, just restore the snapshot. Good virtual machine tools include: VMware, Parallels.
· For many of the ones mentioned above, you can have at least two accounts, two tools, two devices, etc. It is not impossible to completely create an independent virtual identity after you become familiar with them.
I have mentioned a rather extreme point of view before: privacy is not for protection, but for control.
The reason for raising this point of view is because in the current Internet environment, privacy has actually been leaked to a great extent. Fortunately, privacy-related bills have become more and more popular in recent years, and everyone pays more and more attention to them. Everything will indeed work out for the best. But before that, no matter what, when you master the knowledge points I have listed, you will have the ability to control your privacy with ease. If you are used to it on the Internet, you may have several almost independent virtual identities.
human security
Having said all that, talent is the biggest and eternal risk. There is a saying in "The Three-Body Problem": "Weakness and ignorance are not obstacles to survival, arrogance is."
· Don’t be arrogant: If you think you are already strong, just do it yourself. You don’t have to despise everything, especially if you are arrogant enough to challenge hackers around the world. There is no end to learning and there is no end to pitfalls.
· Don’t be greedy: Greed is indeed the driving force for progress in many cases, but you have to think about it, why is this good opportunity left to you? Are you handsome or do you speak nicely? :)
· Don’t be impulsive: Impulse is the devil, you will encounter traps everywhere, rushing without certainty is just gambling.
There are a bunch of points about human nature that I can’t finish talking about, and the key is that I have a lot of problems myself. All I can say is that I was walking on thin ice with trepidation. Below I will focus on a few points that require special attention. They are all related to the flaws of human nature. Bad people use the convenience of some platforms to play with human nature to death.
· Telegram
I have said before that Telegram is the largest dark web. First of all, I have to say that Telegram is too powerful. Its safe, stable, and sufficiently open design has been liked by too many people. But the cultural foundation of Telegram also makes bad people like it very much: Telegram is so easy to use, the user base is large enough, and the functions are open enough. It is very convenient to customize various Bot services. Combined with cryptocurrency, many transaction experiences can surpass those in the Tor network. Those darknet markets. And there are too many fish on it.
The only fields of social accounts are basically similar to username or XX number, and the rest can be completely reused by bad guys. Some social platforms have account authentication mechanisms, such as adding a blue V or something. Open social networking can also use some indicators to see whether it is a real account, such as follow status, published content, content interaction, etc. Closed social confirmation is more troublesome, but the function of introducing groups like Telegram is quite good.
Human nature is like this. Whenever there is a loophole that can be exploited and the benefits are considerable, a bunch of bad people will take advantage of it.
Therefore, there are a lot of phishing traps on social platforms. For example, you are chatting in a group, and suddenly someone who looks like an official customer service chats with you privately (well, any private chat is a mechanism of Telegram, and there is no need to add friend), and then brought out the classic saying of killing pigs, and some people took the bait one after another...
If we go further, we will directly drag you into another group, and the people in it will be fake except for you. But when you look at it, it feels very real. This is what the group cloning technology in black industry refers to.
These are all rudimentary uses of human nature, and more advanced ones will be exploited in combination with vulnerabilities, which is even more difficult to prevent.
· Discord
Discord is a new social platform that has become popular in the past two years. It has basic functions such as chat and group. The core function is an independent community server (not a server as traditionally understood), as the official statement says:
Discord is dedicated to being a place where you talk and hang out with your friends, family, and community. There are millions of different communities on Discord, ranging from small groups of old friends to large servers with thousands of people connected by common interests.
It looks beautiful, but in fact the security design challenges are also very high. The officials are also working hard and have special safety rules and policy instructions:
Unfortunately, many people will not read it carefully. In addition, officials may not always be able to explain some core security issues clearly, because some security issues can only be understood from the perspective of an attacker.
One of them is highlighted below.
There have been so many NFT theft cases on Discord. What are the key points of the attack techniques? If you don't understand this, a bunch of Discord security advice won't be of much use.
The technical point of many projects’ Discord servers being hacked is the so-called Discord Token. In fact, this thing is the authorization field content in the HTTP request header. This thing has existed in Discord for a very long time. For hackers, as long as they find a way to get this Discord Token, they can almost completely control the target's Discord permissions. In other words, if the target is an administrator, a person with administrative permissions, or a robot (Bot), then hackers can use these privileges to do evil.
For example, when an NFT phishing website was released, everyone saw the official announcement and rushed into the phishing website...
Someone may ask, is it OK to add two-factor (2FA) authentication to my Discord account? Definitely a good habit! But it’s impossible to deal with this attack! Discord Token regardless of whether you have 2FA enabled. If you have been tricked, you should change your Discord password immediately so that the Discord Token will be refreshed with the change.
As for how hackers obtained this Discord Token, we have figured out at least three major methods, and we will find an opportunity to write it down later. For ordinary users, there are actually quite a lot of defense suggestions. The core points are: don’t be anxious, don’t be greedy, and verify with multiple parties.
· Fishing from the "official"
Bad guys are really good at taking advantage of the situation to cause trouble, especially taking advantage of the official situation. If you can counterfeit it, try to imitate it as closely as possible, such as the fake customer service mentioned above. Also in early 2022.4, many users of Trezor, a well-known hardware wallet, received phishing emails from trezor.us. In fact, trezor.us is not the official domain name of Trezor. The official domain name of Trezor is just trezor.io. Only the domain name suffix is different. In addition, the following domain names were spread in phishing emails:
There is a "bright spot" in this domain name. If you look carefully, it is not the English letter "e". Very confusing, in fact this is Punycode, the standard description is like this:
A Bootstring encoding of Unicode for Internationalized Domain Names in Applications (IDNA) is the internationalized domain name encoding, which can represent a limited character set of Unicode codes and ASCII codes.
If the trzor looks like this after being untied: xn--trzor-o51b, this is the real body!
The phishing method of Punycode has been actually used a few years ago. For example, in 2018, some users of Binance were tricked.
This kind of phishing with a domain name that looks very similar can fool many people, not to mention more advanced attack methods, such as some official mailboxes being controlled, and an email forgery attack caused by SPF configuration problems in user mailboxes. The source of the email seen by the user has exactly the same official characteristics.
If insiders are doing evil, then users are asking for their own blessings. The project party's internal safety risk control must pay special attention to personnel safety. This is always the most worthwhile cost and energy to build. People are the biggest Trojan horse, but they are also the most overlooked. Some people have really poor safety awareness and are unwilling to make progress in safety. Whoever recruits this kind of person will be in trouble.
· Web3 Privacy Issues
With the popularity of Web3, more and more interesting or boring projects have appeared, such as various Web3 infrastructure, social platforms, etc. Some infrastructures have done massive data analysis, and accidentally discovered various behavioral portraits of the targets of interest, not only on various blockchains, but also on well-known platforms such as Web2. Once the portrait comes out, the target is basically a transparent person. The emergence of Web3 social platforms may also exacerbate such privacy issues.
Think about it, when you play with all these Web3-related things, such as signature binding, various interactions on the chain, etc., will your privacy be leaked more? Many people think not, but in fact, when many pieces are put together, it can actually produce a more comprehensive portrait: which NFTs do you like to collect, which communities do you join, which whitelists are you in, and who are you associated with? Which Web2 accounts are you bound to, what time period are you active in, etc. See, blockchain sometimes makes privacy worse. If you care about privacy, you need to be cautious about anything new and maintain the good habit of isolating your identity.
At this time, if the private key is accidentally stolen, the loss is no longer as simple as funds, but all carefully maintained Web3 rights and interests. We often say that the private key is the identity, and now it seems that it is really the identity.
This is the end of the human safety part. I won’t expand on it any further. You can draw inferences from one example.
Never test human nature.
Blockchain’s ways of doing evil
The emergence of blockchain technology gave birth to the industry we are in now. No matter what you call this industry, chain circle, currency circle, blockchain, cryptocurrency, virtual currency, digital currency, Crypto, Web3, etc., the core of everything Almost all still revolves around blockchain. The most exciting ones are related to financial activities, such as coins, including non-fungible tokens (NFT, also called digital collections).
This industry is incredibly dynamic and attractive, but there are too many ways to do evil. Due to the uniqueness of blockchain, some unique ways of doing evil have also emerged. These evil methods generally include: currency theft, malicious mining, ransomware, dark web transactions, Trojan horse C2 transfer, money laundering, fund disk, gambling, etc. In 2019.1, I made a mind map for reference:
https://github.com/slowmist/Knowledge-Base/blob/master/mindmaps/evil_blockchain.png
At the same time, we are constantly updating and maintaining the SlowMist Hacked blockchain hacked archive, with a large number of case indexes and historical marks:
This manual mentions many safety points. If you can digest them into your own, congratulations. As for these various ways of doing evil, I am not going to expand on them. If you are interested, you should learn to expand them yourself. It’s definitely a good thing to know more, not to mention that new methods of doing evil are always emerging in an endless stream, with constant variations. As your ability grows, I also hope you can participate in making this industry better.
What to do if it's stolen
Since I said it will be a matter of time before you get hacked. So what do you do when you get hacked, or even have your cryptocurrency stolen? I'll simply get to the point. The following steps are not necessarily in this exact order, and sometimes they go back and forth, but this is generally the case.
Stop loss first
Stop loss is to prevent losses from amplifying. This is divided into at least two stages:
· The immediate anxious stage. What is in front of you is definitely a top priority. For example, you have seen that hackers are transferring your assets one after another. What else are you thinking about? Hurry up and transfer the remaining assets safely. If you have experience in trading front-running, then front-run. Look at the type of asset. If it is the kind that can be frozen on the chain, contact us to freeze it as much as possible. If you have the ability to do on-chain tracking and analysis and find that funds have been transferred to the centralized platform, you can contact them to do necessary risk control.
· The post-situation control stage. After the situation is stabilized, the key thing to consider is how to avoid secondary or tertiary injuries.
Protect the scene
If you find something has happened, stay calm, take three deep breaths, and then protect the scene. There are several experiences for reference:
· For Internet-connected devices such as computers and servers, once these are the scene of an accident, the network will be disconnected immediately, but the power will not be shut down (the power supply will continue). Some people say that if it is a destructive virus, if you do not shut down the computer, all the files in the local system will be destroyed by the virus. You are right, if your reaction can be faster than the virus...
· Unless you are capable, wait for professional security personnel to intervene in forensic analysis.
This is very critical. We have encountered many situations where when we intervened to do analysis, the scene was already in a mess, and even key evidence (such as logs and virus files) had been cleaned up. Failure to preserve a well-preserved crime scene will greatly interfere with subsequent analysis and tracing.
Analyze the reasons
The purpose of analyzing the reasons is to understand the opponent and output a portrait of the hacker. At this time, the accident report is very important, also called the post-mortem report (Post Mortem Report). Of course, it is strange to translate Post Mortem Report into post-mortem report in China. We can just call it accident report.
We have encountered many people who come to us to ask us what to do after their coins have been stolen. What is very confusing is that many people have difficulty expressing themselves clearly, let alone issuing a clear incident report. But I think expression can be learned through practice or by copying the gourd. For example, at least explain the following points:
· Summary 1: Who, when, what happened, and how much was the total loss?
· Summary 2: The wallet address, hacker wallet address, currency type, and quantity related to the loss can be clearly understood in a table.
· Process description: This is the most difficult part. Here you need to describe all aspects of the accident process in detail. This will even analyze various traces related to the hacker, and finally output a portrait of the hacker (including the motive for committing evil)
When we are specifically docking, the template will be much more complicated and will be done step by step. Sometimes people's memory also has problems, and they may even deliberately conceal key information, resulting in wasting time or delaying perfect opportunities. Therefore, in actual docking, the consumption is really huge, and we need to use our experience to guide the work. Finally, work with the person who lost the coin or the project party to issue an accident report, and continuously update this accident report.
Traceability
According to Rocca's Law: Any invasion must leave traces. As long as we search carefully, we will always find something. This investigation process is actually forensic analysis and tracing. We will trace the source based on the hacker portrait obtained through forensic analysis, and continue to enrich the hacker portrait. This is a dynamic and iterative process.
Traceability includes two parts:
· On-chain intelligence: Analyze the direction of funds based on wallet addresses, such as entering centralized trading platforms, currency mixing platforms, etc., and monitor and alert new transfers.
· Off-chain intelligence: This part of the intelligence includes: the hacker’s IP, device information, email address and richer information derived from the collision of these points, including behavioral information.
There is a lot of tracking and tracing work based on this intelligence, and even the intervention of law enforcement agencies is required.
Close the case
Of course we all hope for a good ending. Among the public events disclosed in history, we have been involved in the ones that had a good ending. Here are a few examples:
· Lendf.Me, worth $25 million
· SIL Finance, valued at US$12.15 million
· Poly Network, valued at $610 million
We have experienced many unannounced good endings and okay endings. But most of them have bad endings, which is a pity. We have accumulated a lot of valuable experience in these processes and hope to increase the rate of good endings to a higher level in the future.
This part will be briefly mentioned. I am not going to go into details. The amount of knowledge in this area is huge, and I am not good at some of it. According to different scenarios, the abilities we need to master are:
· Smart contract security analysis and evidence collection
· On-chain fund transfer analysis and evidence collection
· Web security analysis and forensics
· Linux server security analysis and forensics
· Windows security analysis and forensics
· macOS security analysis and forensics
· Mobile phone security analysis and forensics
· Malicious code analysis and evidence collection
· Security analysis and forensics of network equipment or platforms
·Personnel safety analysis and evidence collection
·…
This manual covers almost every aspect of safety, but almost all of them are introduction doors.
Misunderstanding
This manual starts by telling you that you need to always be skeptical! Include any knowledge points mentioned in this manual. This is a vibrant industry with huge potential, full of traps and chaos. Here we take a look at some of the misunderstandings. If these misunderstandings are taken as truth without thinking, it is easy to fall into the trap and become part of the chaos.
Code Is Law
Code is law. But often a project (especially related to smart contracts) is hacked or ran away. Few victims hope that code is the law, and they will ultimately rely on real law.
Not Your Keys, Not Your Coins
If it’s not your private key, it’s not your currency. In fact, many users obtained private keys, but were unable to control their private keys. Instead, they lost their coins due to various security issues. Sometimes you will find that it is much safer if the currency is placed on a platform that is large enough and has a good reputation.
In Blockchain We Trust
Because of blockchain, we believe it. In fact, the blockchain itself does have the ability to solve some fundamental trust issues, such as non-tampering, resistance to censorship, etc. If my assets and related activities are on the blockchain, I can tacitly believe that no one can take my assets without authorization. Assets, tampering with my activity. But reality is often cruel. Firstly, not all blockchains have the ability to achieve these fundamental points. Secondly, human nature is always the biggest breakthrough point. Many hacking techniques are beyond the imagination of most people. Although attack and defense are cost confrontations, for example, if your assets are not large enough, no hacker will bother to hack you in a targeted manner. However, if there are multiple such you, then it is not possible. It's very profitable.
My security advice is simple: keep the default distrust of everything (that is, the default suspicion of everything), and do a good job of continuous verification. Verification is a critical security action. Continuous verification tells you that security is not static. Just because there is no problem at this time does not mean that there will be no problems in the future. Verifying your ability is the biggest test for yourself, but it is very interesting and you will master enough knowledge. When you are strong enough, no one can easily bully you.
Cryptographic security is security
Cryptography is indeed strong and important. Without the efforts of so many cryptographers and so many solid cryptographic algorithms and engineering implementations, our current communication technology, Internet technology, and blockchain technology would be useless. Unfortunately, some people regard cryptographic security as all security, so some very strange questions will arise:
Doesn’t the blockchain claim to be very secure? Doesn’t the private key say how many billions of billions of years it will take to crack it? Why did the FBI crack darknet Bitcoin? Why are Jay Chou's NFTs stolen?
I can tolerate these questions... What I can't tolerate is that there are so-called security people who use cryptography security to deceive the public. They talk about military-level encryption, palace-level encryption, and universe-level encryption. The system is extremely safe, and hackers can't do anything about it.
Hackers can’t be bothered to care about you…
It's embarrassing to be hacked
Being hacked does make you feel very complicated, and it does feel embarrassing. But you need to understand that being hacked is a universal phenomenon, without exception. There is no need to laugh at fifty steps and laugh at a hundred steps, and there is no need to avoid covering up if you feel embarrassed.
After being hacked, if you only need to be responsible for yourself, then feel free; if you need to be responsible for some or many people, a transparent and open attitude and responsible approach to handling hacks are very critical. Although it may attract ridicule, doubts, and even accusations that you are directing and acting in this hacking incident.
A transparent, open and constantly updated progress of hacking, coupled with painful lessons learned, you will always attract good luck. You can also think of it this way: If your project is not even famous, who will hack you? The shameful thing is not being hacked, the shameful thing is: being arrogant.
Although being hacked is a common phenomenon in 100%, because most of them are small pits, stepping on the small pits will accelerate growth, but the big pits must be avoided as much as possible.
update immediately
Several times in this manual I recommend that you pay attention to updates and update as soon as security updates are available. So if you think about it carefully, is my statement universal?
Here's the thing: most of the time, "update now" is the right thing to do when it comes to security. But sometimes, an update fixes one problem and may introduce another. There are many such cases in history, you can search for them yourself. Let me give you one example, about iPhone and Google Authenticator:
There is a risk after the iPhone's new version of iOS 15 system is upgraded. The information in the Google Authenticator may be cleared or double. If a double is found, do not delete the duplicate entries. This will cause the information in the Google Authenticator to be reopened. All information is lost. It is recommended that those who have not upgraded to iOS 15 and are using Google Authenticator should back up before upgrading.
Later, Google updated Authenticator to completely solve this problem.
In addition to this point, I do not recommend frequent wallet updates, especially wallets with heavy assets. Unless there is a major security update that requires you to update the wallet, or there are very important functions that require you to update. This requires you to make your own risk assessment and decision.
Summarize
This manual opens with this picture :)
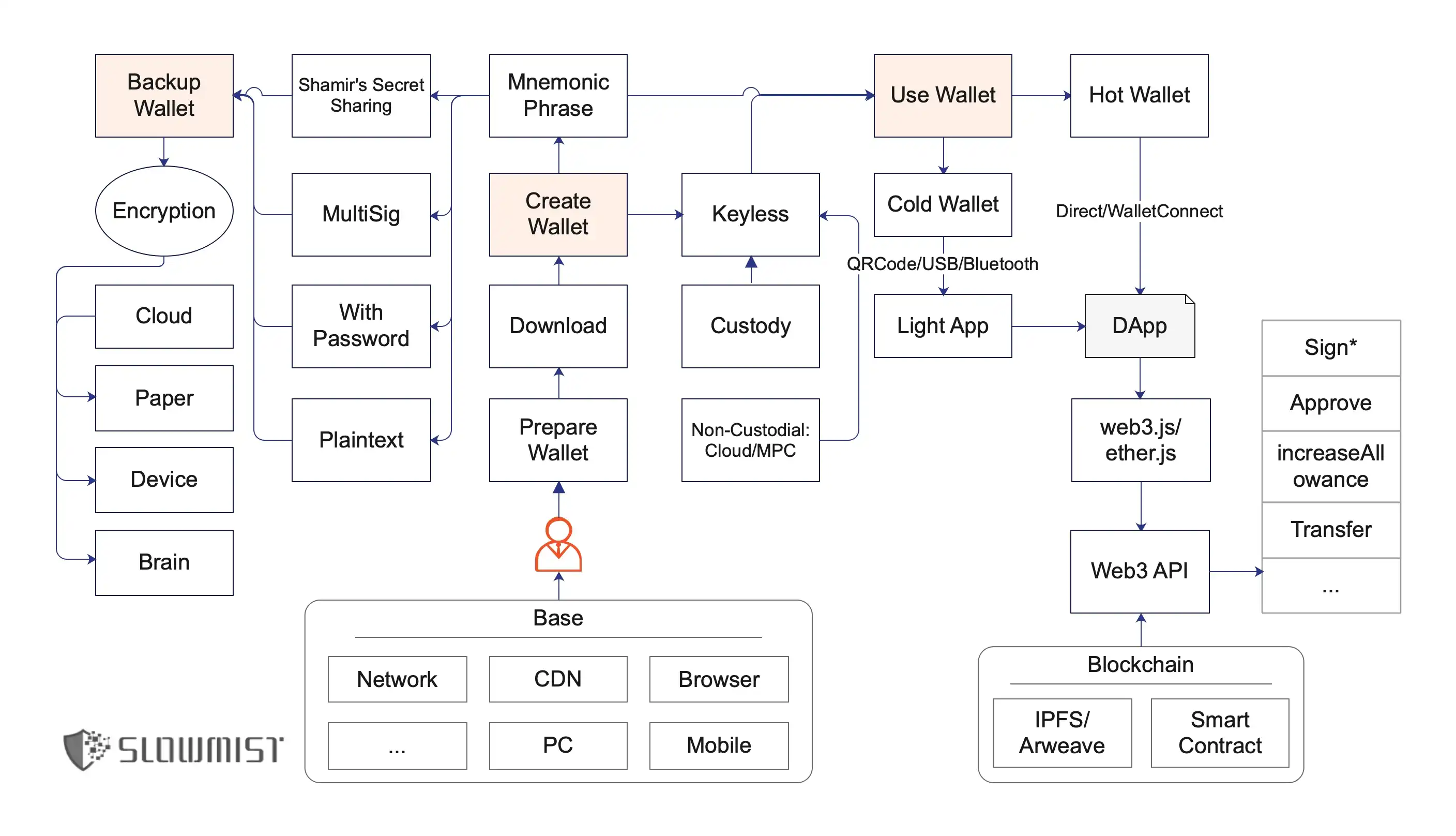
Did you notice? I specially marked the people in the picture red to remind you repeatedly: people are the basis of all things (called the "anthropic principle" in the field of cosmology). Whether it is human safety or safe driving ability, it ultimately depends on you. Yes, when you are strong enough, no one can easily bully you.
I followed the diagram and explained many security points in the three major processes from creating a wallet to backing up the wallet and then using the wallet. Then I introduced traditional privacy protection. I said that these traditional ones are the cornerstones and the cornerstones for us to play safely in the blockchain ecosystem. The human security part cannot be mentioned enough. It’s good to know more about the various ways of doing evil. Even if you step on the traps a few times, many of the safety awareness you have on paper will really become your safety experience. There is no absolute security, so I explained what to do if it is stolen. I don’t want you to be stolen, but if it happens, I hope this safety guide after being stolen can help you. Finally, I will talk about some misunderstandings. The simple intention is that I hope you have your own critical thinking, because the world is beautiful, but there are also many bad things.
It's been a long time since I wrote so many words. The last time was 10 years ago. My book "Web Front-end Hacking Technology Revealed" was quite refreshing. After playing in web security offense and defense for many years, I have also been playing in cyberspace security for many years. I led a team to build a cyberspace search engine called ZoomEye. I can be regarded as someone who has dabbled in many fields of security attack and defense, but I can only say that I am proficient in it.
Now when it comes to blockchain security, I and SlowMist are all at the forefront. There are so many cases encountered over the years that it is almost possible to experience that trance feeling every week. It would be a pity not to record many of my experiences. Finally, at the urging of several friends, this manual was born.
After you finish reading this manual, you must practice it, become proficient, and draw inferences from one example. If you have your own discoveries or experiences later, I hope you can contribute as well. If you feel sensitive, you can desensitize it appropriately and remain anonymous.
Finally, I would like to acknowledge the maturation of security and privacy-related legislation and enforcement around the world; the efforts of generations of cryptographers, engineers, righteous hackers, and all those involved in creating things that make this world a better place, one of whom is Satoshi Nakamoto.
attached
Safety rules and principles
This manual mentions relevant safety rules and principles, which are specially organized as follows. Many of them are integrated into large paragraphs, so I won't make any special refinements.
Two major safety rules:
· Zero trust. Simply put, be skeptical, and always be skeptical.
· Continuous verification. If you want to believe, you must have the ability to verify your doubts and develop this ability into a habit.
Safety principles:
· For knowledge on the Internet, refer to information from at least two sources for everything, support each other, and always remain skeptical.
· Segregate well, that is, don’t put eggs in one basket.
· For wallets that contain important assets, do not update them easily, just use them enough.
· What you see is what you sign. That is, the content you see is what you expected to sign. When your signature is sent, the result should be what you expected, and it will never be a slap in the face afterwards.
· Pay attention to system security updates and act immediately when security updates are available.
· Not messing with the process has actually eliminated most of the risks.
Contributor
Thanks to the contributors, this list will continue to be updated. If you have any ideas, please contact me:
cosine,Twitter(@evilcos), immediately (@ cosine.jpg)
Contributors:
Mrs. Cosine
Slow Mist, Twitter (@SlowMist_Team), such as: Pds, Johan, Kong, Kirk, Thinking, Blue, Lisa, Keywolf…
immediately
some anonymous friends
…
As long as there is help that is adopted and included in this manual, such as: providing specific defense suggestions and cases; translation work; correction of major errors, etc.


