The most daring cryptocurrency theft gang in history, the hacker group Lazarus Group, money laundering analysis
Written by Beosin
Earlier, a confidential UN report obtained by Reuters showed that the North Korean hacker group Lazarus GroupcryptocurrencyexchangestealAfter withdrawing the funds, $147.5 million was laundered through the virtual currency platform Tornado Cash in March this year.
The monitors told the UN Security Council sanctions committee in a previous filing that they have been investigating 97 suspected North Korean hacking attacks oncryptocurrency公司的网络攻击,价值约 36 亿美元。其中包括去年年底的一次攻击,HTX 加密货币交易所的 1.475 亿美元被steal, and then completed the money laundering in March this year.
The United States imposed sanctions on Tornado Cash in 2022, and in 2023, its two co-founders were charged with facilitating the laundering of more than $1 billion, including by the Lazarus Group, a cybercrime organization linked to North Korea.
According to an investigation by cryptocurrency sleuth ZachXBT, the Lazarus Group laundered $200 million worth of cryptocurrency into fiat currency between August 2020 and October 2023.
NetworkSafetyIn the field of cybersecurity, the Lazarus Group has long been accused of large-scale cyberattacks and financial crimes. Their targets are not limited to specific industries or regions, but are spread all over the world, from banking systems to cryptocurrency exchanges, from government agencies to private enterprises. Next, we will focus on analyzing several typical attack cases to reveal how the Lazarus Group successfully carried out these amazing attacks through its complex strategies and technical means.
Lazarus Group conducts social engineering and phishing attacks
This case comes from relevant European media reports that Lazarus had previously targeted military and aerospace companies in Europe and the Middle East, posting recruitment advertisements on platforms such as LinkedIn to deceive employees, requiring job seekers to download PDFs with executable files deployed, and then carry out phishing attacks.
Both social engineering and phishing attacks attempt to use psychological manipulation to trick victims into letting their guard down and performing actions, such as clicking a link or downloading a file, that compromise theirSafety.
Their malware enables agents to target vulnerabilities in victims' systems andstealRetrieve sensitive information.
Lazarus used a similar method in a six-month operation against cryptocurrency payment provider CoinsPaid, which resulted in thesteal $37 million.
Throughout the campaign, it sent fake job offers to engineers, launched technical attacks such as distributed denial of service, and submitted many possible passwords for brute force cracking.
Create CoinBerry, Unibright and other attacks
On August 24, 2020, Canadian cryptocurrency exchange CoinBerry walletStolen.
Hacker Address:
0xA06957c9C8871ff248326A1DA552213AB26A11AE
On September 11, 2020, due to the private key leak, multiplewalletAn unauthorized transfer of $400,000 occurred.
Hacker Address:
0x6C6357F30FCc3517c2E7876BC609e6d7d5b0Df43
2020 年 10 月 6 日,由于安全漏洞,CoinMetro 热钱包中未经授权转移了价值 75 万美元的加密资产。
Hacker Address:
0x044bf69ae74fcd8d1fc11da28adbad82bbb42351
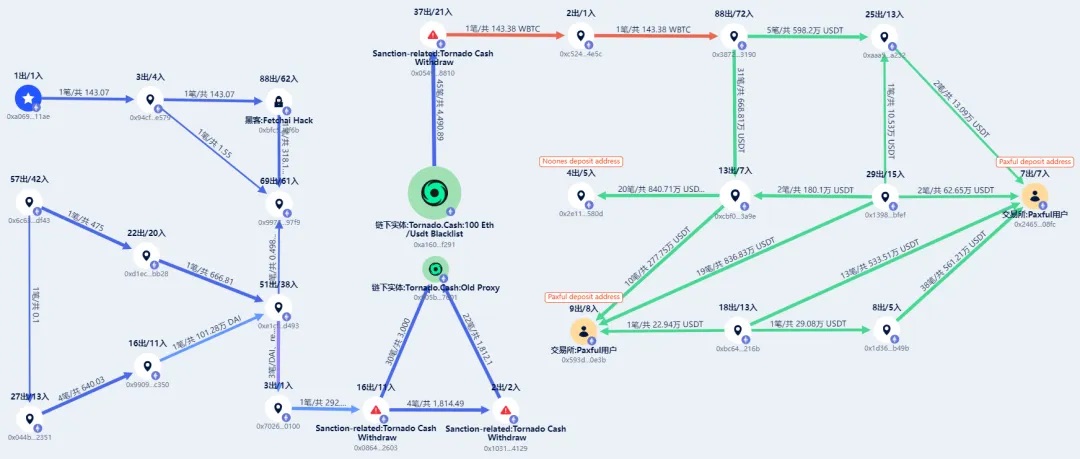
Beosin KYT: Stolen Funds Flow Chart
In early 2021, funds from various attacks were funneled to the following addresses:
0x0864b5ef4d8086cd0062306f39adea5da5bd2603.
On January 11, 2021, the 0x0864b5 address deposited 3,000 ETH in Tornado Cash, and then deposited more than 1,800 ETH into Tornado Cash through the 0x1031ffaf5d00c6bc1ee0978eb7ec196b1d164129 address.
Subsequently, from January 11 to January 15, nearly 4,500 ETH were withdrawn from Tornado Cash to the address 0x05492cbc8fb228103744ecca0df62473b2858810.
到 2023 年,攻击者经过多次转移兑换,最终汇集到了其他安全事件资金归集提现的地址,根据资金追踪图可以看到,攻击者陆续将盗取的资金发送至 Noones deposit address 以及 Paxful deposit address。
Nexus Mutual founder (Hugh Karp) hacked
On December 14, 2020, Nexus Mutual founder Hugh Karp had 370,000 NXM (US$8.3 million) stolen.
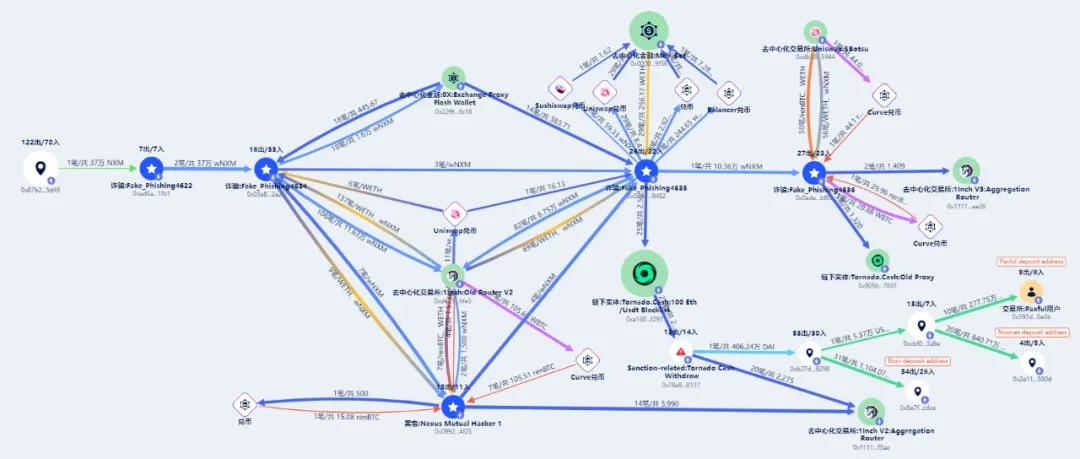
Beosin KYT: Stolen Funds Flow Chart
The stolen funds were transferred between the following addresses and exchanged for other funds.
0xad6a4ace6dcc21c93ca9dbc8a21c7d3a726c1fb1
0x03e89f2e1ebcea5d94c1b530f638cea3950c2e2b
0x09923e35f19687a524bbca7d42b92b6748534f25
0x0784051d5136a5ccb47ddb3a15243890f5268482
0x0adab45946372c2be1b94eead4b385210a8ebf0b
Lazarus Group used these addresses to confuse, disperse, and aggregate funds. For example, some funds were transferred to the Bitcoin chain through a cross-chain, and then transferred back to the Ethereum chain through a series of transfers. After that, they were mixed through a mixing platform and then sent to a withdrawal platform.
From December 16 to December 20, 2020, one of the hacker addresses 0x078405 sent more than 2,500 ETH to Tornado Cash. A few hours later, based on feature association, it was found that the address 0x78a9903af04c8e887df5290c91917f71ae028137 started withdrawing funds.
The hacker transferred and exchanged part of the funds to the address for fund collection and withdrawal involved in the previous incident.
Afterwards, from May to July 2021, the attacker transferred 11 million USDT to the Bixin deposit address.
From February to March 2023, the attacker used 0xcbf04b011eebc684d380db5f8e661685150e3a9eXiaobai Navigation address, send 2.77 million USDT to the Paxful deposit address.
From April to June 2023, the attacker sent 8.4 million USDT to the Noones deposit address through the 0xcbf04b011eebc684d380db5f8e661685150e3a9e address.
Steadefi and CoinShift hack
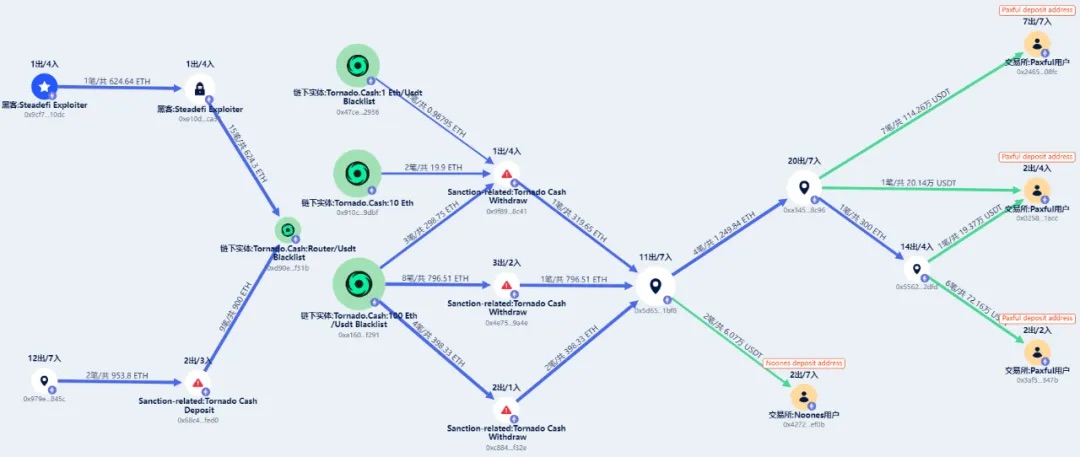
Beosin KYT: Stolen Funds Flow Chart
Steadefi 事件攻击地址
0x9cf71f2ff126b9743319b60d2d873f0e508810dc
Coinshift attack address
0x979ec2af1aa190143d294b0bfc7ec35d169d845c
In August 2023, 624 stolen ETH from the Steadefi incident were transferred to Tornado Cash. In the same month, 900 stolen ETH from the Coinshift incident were transferred to Tornado Cash.
After transferring ETH to Tornado Cash, immediately withdraw the funds to the following addresses:
0x9f8941cd7229aa3047f05a7ee25c7ce13cbb8c41
0x4e75c46c299ddc74bac808a34a778c863bb59a4e
0xc884cf2fb3420420ed1f3578eaecbde53468f32e
On October 12, 2023, the above three addresses sent the funds withdrawn from Tornado Cash to the 0x5d65aeb2bd903bee822b7069c1c52de838f11bf8 address.
In November 2023, the 0x5d65ae address began to transfer funds, and eventually sent the funds to the Paxful deposit address and Noones deposit address through transit and exchange.
Event Summary
The above introduces the dynamics of the North Korean hacker Lazarus Group in the past few years, and analyzes and summarizes its money laundering methods: After stealing crypto assets, Lazarus Group basically confuses funds by transferring them back and forth across chains and then into mixers such as Tornado Cash. After the obfuscation, Lazarus Group extracts the stolen assets to the target address and sends them to a fixed group of addresses for withdrawal operations. Previously, the stolen crypto assets were basically deposited into Paxful deposit addresses and Noones deposit addresses, and then the crypto assets were exchanged for legal currency through OTC services.
Under the continuous and large-scale attacks of Lazarus Group, the Web3 industry faces great security challenges. Beosin continues to pay attention to this hacker group and will further track its dynamics and money laundering methods to help project owners, regulators and law enforcement agencies combat such crimes and recover stolen assets.
The article comes from the Internet:The most daring cryptocurrency theft gang in history, the hacker group Lazarus Group, money laundering analysis
Related recommendation: Ethereum upgrade: Basic knowledge about consensus (Part 2)
This is an authoritative technical book on the Ethereum Proof of Stake protocol. It will start with some preliminary content and cover some consensus basics that are not limited to Ethereum. Written by: Ben Edgington Translated by: Tiao This article is the second half of the "Basics of Consensus" chapter. For the previous article, please see "Upgrading Ethereum: Basics of Consensus" The fork choice rule is just like...