Detailed introduction to RGB, BitVM, and Nostr
Author: Zhejiang University Chain Association, BiHelix, ScaleBit & BTC Security Lab
Intro: Why BTC L2
The explosion of the inscription ecosystem in 2023 has rapidly increased the priority of BTC scalability issues.BlockchainThe method of giving Bitcoin additional attributes or meanings by adding additional information, such as BRC20, causes congestion in native Bitcoin transactions, BTC L2 作为解决这个问题的关键,会成为2024年的关键叙事。本文将带大家深入了解 RGB、BitVM 以及基于闪电网络的 Nostr 这三个潜力巨大的 BTC L2 解决方案。
RGB Protocol
What is RGB
RGB is a scalable and confidential smart contract for Bitcoin and Lightning Network.contractThe protocol was developed by the LNP/BP Standards Association. It adopts the concepts of private and common ownership and is a Turing-complete, trustless distributed computing form that does not require the introduction ofTokenIt should be clear that there is no network in RGB, nor is thereBlockchain, which is a client-side authentication technology, is aPartial state intelligencecontractsystem.
RGB protocol development history
RGB Protocol History
RGB 最初由来自 BHB Network 的 Giacomo Zucco 于2016 年设想为“基于非区块链的资产系统”,同年,Peter Todd提出了一次性密封(Single-use seal)和客户端验证(Client-Side Validation)的概念。受到这些重要思想的启发,RGB 于 2018 年被提出。2019 年,核心开发者 Maxim Orlovsky 开始推动RGB,并参与了了绝大部分 RGB 协议的代码开发和底层标准设计。Maxim Orlovsky和Giacomo Zucco共同成立了LNP/BP 标准协会(https://www.lnp-bp.org),旨在推动 RGB 从概念诞生到实际应用的阶段。该协会得到 Fulgur Ventures 、 Bitfinex 、Hojo 基金会、Pandora Prime 和 DIBA 的支持。经过大量开发工作, 2023 年 4 月,RGB 发布了版本 V0.10 ,这是第一个稳定可用的版本。2024年1月,RGB 核心开发者表示会在上半年尽早推出版本V0.11。
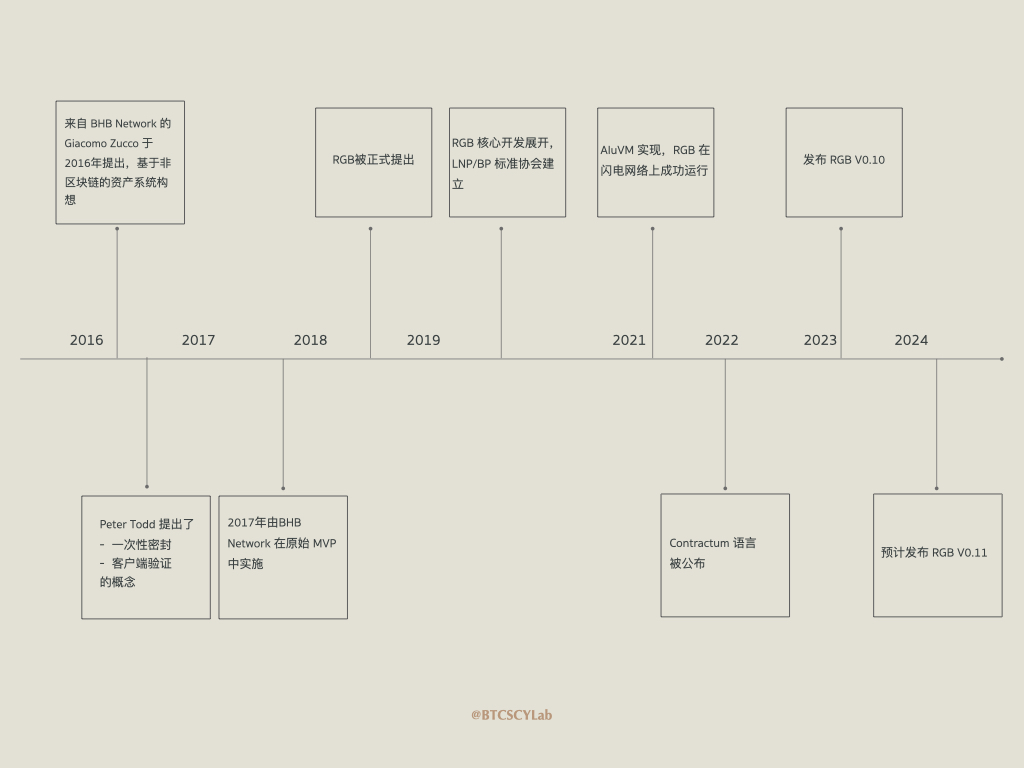
RGB Protocol Latest Development
The new features of RGB V0.10 have been analyzed in detail in other research reports. V0.11 has not yet been officially launched. Here are some of the features that developers andCommunityLatest News:
• Support for L-BTC will be added soon
• Interoperability and cross-chain bridges between RGB assets and Liquid assets will be updated
However, RGB V0.11 will be incompatible with V0.10, which will result in a high migration cost for current projects. At the same time, due to the slow development progress, many projects are currently waiting for the release of V0.11.
RGB design concept and operation principle
RGB 智能合约采用客户端验证,这意味着所有数据都保存在比特币交易之外,即比特币区块链或闪电通道状态。这使得系统能够在闪电网络之上运行,而无需对 BTC 主网或闪电网络协议进行任何更改。这为协议的可扩展性和隐私性奠定了基础。
RGB uses a one-time seal defined on Bitcoin UTXO, which provides any party with the smart contract state history with the ability to verify its uniqueness. In other words, RGB leverages Bitcoin Script to implement itsSafetyModel and definition of ownership and access rights.
RGB is a directed acyclic graph (DAG) of state transitions where contracts are completely isolated from each other and no one except the contract owner (or parties to whom the owner discloses contract information) knows about its existence.
|
A directed acyclic graph (DAG) is a special graph structure that can be used to explain complex systems or relationships in a vivid way. We can imagine each edge in a directed acyclic graph as a one-way street in a city. This is the concept of "directed". And suppose that on these roads, no matter how you drive, you can never return to the starting point to form a closed loop, which meansXiaobai NavigationThis means "no cycle". In a directed acyclic graph, the same is true. There is no sequence of nodes that allows you to start from a node, go through a series of edges, and then return to this node. Applying this concept to the RGB system, we can view each contract as a node in the graph, and the relationship between contracts (such as the transfer of ownership) can be viewed as directed edges. This structure ensures that the relationship between contracts is clear and orderly, and does not form a closed loop, that is, a contract will not directly or indirectly affect itself. |
This design ensures that the commitments in state transfer are unique and cannot be tampered with, prevents double spending, and achieves effective and consistent state transfer.
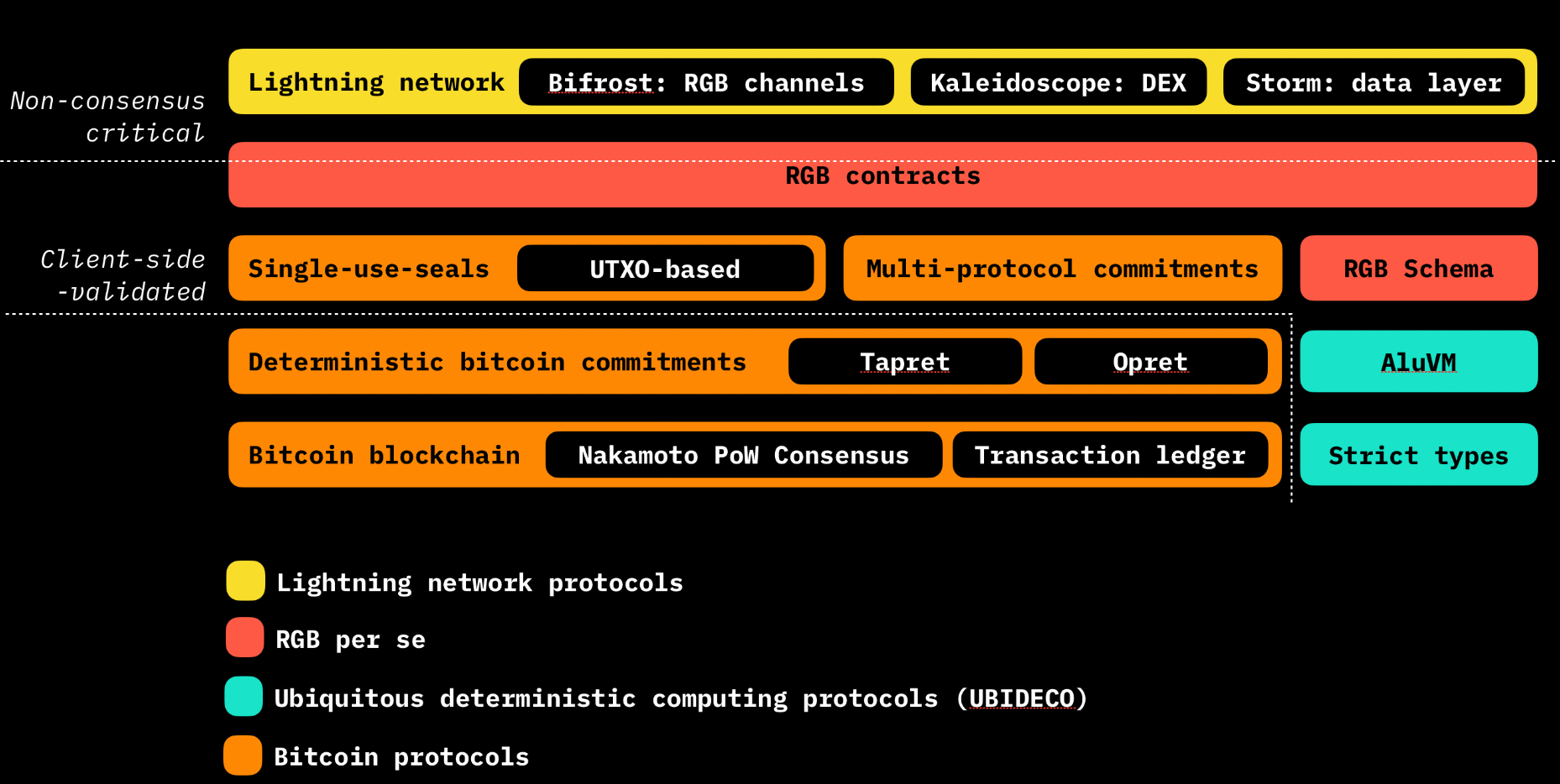
In-depth RGB contract
After understanding the basic idea of RGB architecture design, let's look at the contract part. In the current world of smart contracts, smart contract creators are required to organize or perform the development of smart contract code on their own. In RGB's design philosophy, this is a bad practice that will lead to higher contract code vulnerabilities and multiple hacker attacks. Therefore, RGB intends to reduce the risk of vulnerabilities and audit requirements in development, and introduces the concept of "Contract Schema". "Contract Schema" is the actual code of the smart contract, which can be used by issuers as a "contract template" without requiring them to encode or audit custom code written for them by a random outsourcer.
Flexible scalability and good interoperability
The RGB contract isDeclarativeThis means that the logic of the contract is not defined by a series of commands or steps, but by a set of rules that describe its behavior and state transitions, which is a directed acyclic graph (DAG) of state changes.Local State Operations, is the key to Schema. The operations in the RGB contract are local, not global. Each node (or state) has its own rules and is only responsible for its own state transitions. This is different from the global algorithm on platforms such as Ethereum, which requires each state to follow the same algorithm. This feature makes RGB flexible and scalable, while also having good interoperability.
Easy smart contract writing
Schema defines what types of global and owned states, seals, and metadata are allowed in state transitions. RGB uses the Contractum language to program RGB Schemas and AluVM (arithmetic logic unit virtual machine), which simplifies the writing of RGB smart contracts. AluVM is register-based and does not provide random memory access. It is very suitable for smart contracts, remote code execution, distributed and edge computing, and provides a foundation for various advanced smart contract use cases.
How to ensure RGBSafetyand privacy
From the design of RGB itself
• Privacy without global broadcast: As mentioned above, RGB’s client-side verification means that the verification process only occurs between directly involved peers, rather than the entire network. This non-global broadcast method enhances privacy and censorship resistance, because the details of the contract state are only visible to the relevant participants, and miners cannot see the transaction details.
• Data privacy in sandbox environment: On the other hand, RGB stores all operational data in stash. Since RGB is not blockchain-based, storage is not replicated to other peer nodes. Storage controlled locally by users reduces the risk of external attacks and data leakage, ensuring data privacy. RGB is a computing platform that isolates each program (“smart contract”) in its sandbox environment, which provides better scalability and security than blockchain-based platforms.Safetysex.
• Similarly, off-chain data also means there is a risk of loss.
• 验证和存储以外,发票系统也能确保安全和隐私。RGB 中的合约操作通过创建发票来进行,发票可以包含多种合约操作请求。通过让用户明确指定和验证合约操作,提高了操作的准确性和安全性。同时,发票系统支持在用户之间私下传输合约操作请求,增强交易隐私。通过发票和特定的命令来执行状态转移,如代币转移。
From the perspective of interaction with BTC
• RGB is designed to be highly bound to UTXO. In the process of interacting with the BTC mainnet, users create off-chain contracts to issue RGB assets and assign them to Bitcoin's UTXO, which is very similar to the Lightning Network. Asset transfers, contract interactions and verifications are then performed off-chain in the manner described above.
• RGB benefits from the better multi-signatures, adapter-based signature protocols, and point time lock contracts (PTLCs) enabled by Schnorr signatures, but its benefits are purely based on Bitcoin’s benefits (i.e. indirect). RGB does not have anything internally that needs to be signed (so Schnorr does not change anything internally), nor does it use Bitcoin script (so the new Tapscript has no use).
BTC Security Lab, co-founded by ScaleBit, is a dedicated BTC security laboratory that is working on studying the latest developments in the RGB protocol, aiming to protect its contract security and jointly promote the growing updating and growth of the RGB protocol and the construction of infrastructure for the BTC ecosystem.
List of RGB Ecosystem Projects
1. BiHelix
Official website: https://www.bihelix.net/
BiHelix is a Bitcoin ecological infrastructure that builds optimized nodes based on the Bitcoin native blockchain, combined with the RGB protocol and the Lightning Network. It aims to make it easier for developers to use, increase the use cases of Bitcoin, and solve the challenges of scalability and Turing incompleteness faced by the Bitcoin blockchain.exchange, users to create a fairer decentralized crypto world. As the first infrastructure built on the RGB protocol, BiHelix will create the next generation of large-scale Bitcoin application scenarios. Currently, the project has not yet started interaction and is in the research and development stage, so stay tuned.
Project Features
1. Low user threshold
Using the SLR (Security-Lightning-RGB) protocol, RGB and the Lightning Network are repackaged, and innovative solutions for Lightning nodes are introduced to achieve global universal payment.
2. High reliability and high scalability
It adopts a mature cloud service architecture and makes full use of the features of rust-lightning to support the functions of the channel factory, efficiently manage channels, and create channels in batches.
3. Security and Privacy Protection
Transfer and store state data off-chain using recursionZero knowledge proofTechnologies such as ETH/USD randomize multi-part payments and path selection to achieve privacy protection.
4. Developer-friendly
Provides complete development tools, including open source development documents and tools, and introduces the Schema social consensus mechanism so that developers can easily build applications.
2. Iris Wallet
Official website:Link
IRIS Wallet, the first Android wallet developed by the Bitfinex team wallet,致力于 RGB 集成和 RGB 相关工具,支持可替代和不可替代资产(fungible and non-fungible assets)。 Iris Wallet 支持从发行到支出和接收的 RGB 资产操作,将所有功能包装在一个熟悉的钱包应用程序中,并尽可能多地抽象出技术细节。目前这还是一个实验性应用程序,建议仅用于少量比特币和低价值资产。
3. DIBA
Official website:https://diba.io/
DIBA is the first NFT marketplace on Bitcoin using RGB Protocol’s smart contracts and the Lightning Network. It aims to help shape the understanding of non-custodial art assets on the Bitcoin blockchain.
4. Bitmask
Official website:https://bitmask.app/
This wallet was created by DIBA and is the first NFT wallet in the RGB ecosystem. It can be run in a web browser and interact with RGB contracts similar to MetaMask on Ethereum. Currently, it is updated frequently and is waiting for the release of V0.11.
5. Pandora Prime Inc
Official website:https://pandoraprime.ch/
Pandora Prime is a Swiss company based in Verify Valley and a founding member of LNP/BP.
Pandora Prime is committed to pioneering Bitcoin Finance using a combination of RGB smart contracts and the Lightning Network. They started with programmable assets on Bitcoin (RGBTC and CHFN), which can be expanded to VISA/MasterCard levels in terms of transaction throughput through the Lightning Network, while providing facilities to easily exchange these assets. Currently, their products include MyCitadel (wallet), RGB Explorer (browser), and Pandora Network, etc.
6. MyCitadel
Official website:https://mycitadel.io/
MyCitadel is a brand of Pandora Prime. MyCitadel is the first GUI wallet that supports RGB, created by RGB developers in 2021. It provides cross-platform desktop wallets and iOS/iPad wallets. The mobile wallet can handle fungible RGB assets.
7. RGB Explorer
Official website:https://rgbex.io/
RGB Explorer is the first browser developed by Pandora Prime that provides RGB asset registration and smart contracts. Currently, it supports RGB 20, RGB 21, and RGB 25, and can display four assets: LNPBP, RGBTC, dCHF, and RGBEX.
8. Bitlight Labs (formerly Cosminmart)
Official website:https://bitlightlabs.com/
BitlightLabs develops infrastructure based on the RGB protocol and is preparing to deploy multiple applications on the Lightning Network, including the RGB utility wallet Bitlight Wallet and Bitswap, which builds the BitcoinFi automated market maker on the Lightning Network and the RGB protocol.
10. RGB Memes& NFT
10.1 PPRGB
X: @PepeRgb20
PPRGB is currently issued on the Liquid network and will be mapped to RGB after the RGBV0.11 version is released (RGB v0.11 is also working on code functions related to docking with Liquid).
10.2 MRGB Inscription
MRGB inscription is a token for client state verification and smart contract system based on RGB protocol. The token runs on the second and third layers (off-chain) of Bitcoin ecosystem, and will provide open source underlying protocol code, enabling all BRC20 public chains to use the system directly.
This innovation will bring great potential to the BRC20 public chain, including reducing GAS consumption, speeding up transactions, and improving overall performance. By adopting the MRGB system, the BRC20 public chain will be able to process transactions more efficiently and reduce transaction costs for users. At the same time, the MRGB inscription token will also be used as a consumable in the transaction process, thereby increasing the liquidity and scalability of BTC.
10.3Single-Use-Seal
Seal is a 10k PFP collection, rare UDA and tokens on RGB20 and RGB21. The name is taken from the Single Use Seal proposed by Peter Todd. It is currently waiting for the Bitlight and Bitmask wallets to update the v0.11 RGB version, after which it will be issued on it.
10.4Bitman
X: @bitmancity
会在diba上发行 10k UDA,可能是是 wl+public sale,宗旨是“传递btc的精神”,项目立意不错,会发 wl 给 BTC 生态贡献者,公售大部分捐给 LNP/BP。
BitVM
Why BitVM?
The Bitcoin Virtual Machine (Bitcoin Virtual Machine) introduces a system that can verify any computation on the Bitcoin blockchain without compromising its security or changing the network. This development opens up new possibilities for complex computations such as Turing-completeSmart ContractsThis opens the door for all computations to be processed off-chain to reduce congestion on the Bitcoin blockchain.
"To put it simply, BitVM is a computational model that can express Turing-complete contracts on the Bitcoin network." Like RGB, BitVM does not require modifying the network's consensus rules.
On October 9, 2023, Robin Linus, co-founder of blockchain developer ZeroSync, announced BitVM WhitepaperCompared to RGB, BitVM is much younger.
BitVM design architecture
Architecture
Similar to Optimistic Rollups and the MATT proposal (Merkelize All The Things), based on fraud proofs and challenge-response protocols, there is no need to change Bitcoin's consensus rules. BitVM proves that Bitcoin is Turing complete in large Taptrees that encode fraud proofs.
Gate circuit design
Bit Value Commitment is the most basic component, allowing the committer to set the value of a specific bit to "0" or "1". Any computable function can be represented as a Boolean circuit, forming a logic gate commitment. It is built through NAND gates (universal logic gates), each with its own commitment. Any circuit can be expressed through the combination of gate commitments. Each execution step is committed in the Tapleaf and combined in the same Taproot address.
BitVM leverages Bitcoin's Taproot upgrade to implement its functionality by creating a structure similar to a binary circuit (called a taptree). In this system, the spending conditions of each UTXO are represented by instructions in the Script script, forming the basic unit of the program. These instructions generate binary outputs (0 or 1) within the Taproot address, thereby constructing the entire taptree. The output of the taptree can be regarded as the result of the operation of a binary circuit, similar to an executable program. The complexity of the program that the taptree can execute depends on the number and complexity of the Taproot addresses that make it up. In short, BitVM realizes the ability to run more complex programs on the Bitcoin network by converting Bitcoin's Script instructions into binary operations.
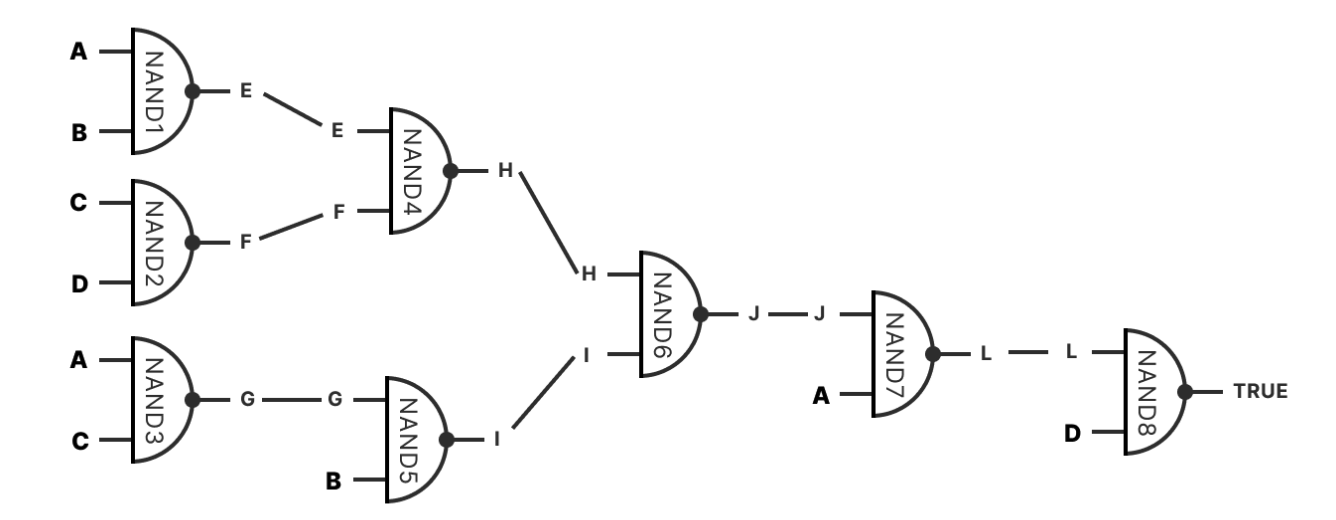
There are two parties involved
The current model is limited to two parties and cannot currently expand the number of participants. In addition, in order for BitVM to work properly, a large amount of pre-signing (off-chain calculations) is required, which makes BitVM actually quite complex and may have inefficiencies.
Fraud Proofs and Challenge-Response Protocols
The prover and challenger both deposit an equal amount of BTC in a transaction for a bet (as input), and the output of this transaction will contain a logic circuit. The rebuttal of false claims is achieved by pre-signing a series of transactions in the setup phase. BitVM is compared to Optimistic Rollups because it performs most of the computation off-chain and submits some of the computations to the chain to resolve disputes when disputes arise.
• Optimistic rollups are a layer 2 scaling solution that reduces the load on the base layer by moving computation and data storage off-chain. It then bundles multiple transactions and publishes them to the main chain.
• Optimistic rollups assume that all transactions are valid. However, if a network participant realizes that dishonesty has occurred, they can issue a fraud proof. A fraud proof is evidence that someone's calculations were inaccurate. They are generated after an inspection.
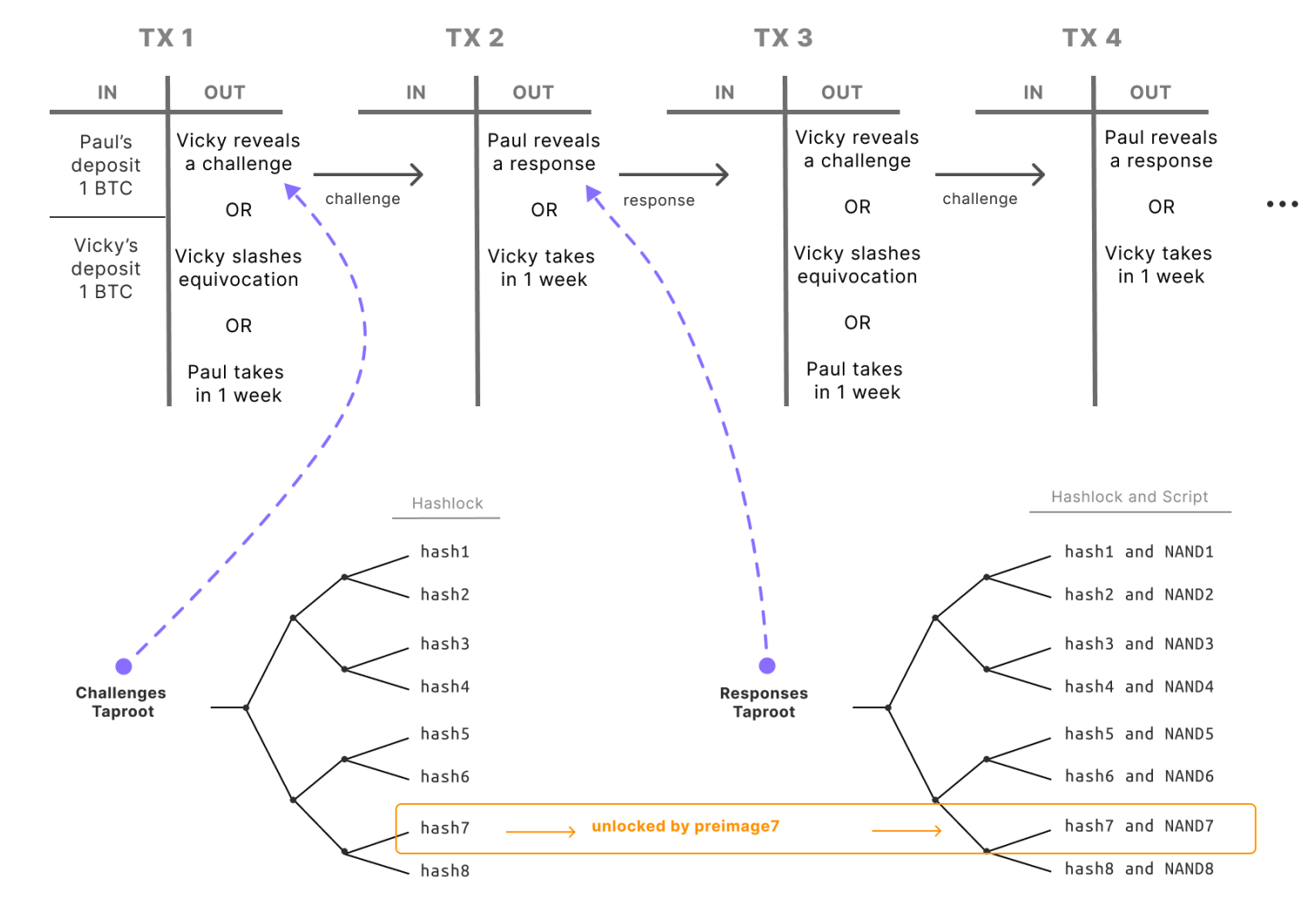
Off-chain computing
Almost all activity on BitVM occurs off-chain. This includes launching computational tasks, sharing data, and verifying submitted claims. BitVM does not typically run computations on the Bitcoin blockchain. Computational activity and verification are only published on-chain when there is a dispute due to suspected fraud. However, if there is a dispute, a small portion of the dispute process does run on-chain, just enough to figure out which party is being dishonest.
With the above prerequisites, we can better understand BitVM Interaction between the two partiesThe specific principle.
BitVM's two-party interaction model involves a prover and a verifier. In this system, the prover first creates and submits a smart contract or program, and then sends funds to a jointly controlled master root address. These funds are kept in a 2-of-2 multi-signature manner. The prover also needs to share enough information with the verifier to prove that their program can produce the promised output.
The verifier’s task is to run the prover’s code and verify that the output is as expected. If the output is not as expected, the verifier will challenge the prover. This challenge-response interaction involves the exchange of data off-chain and the use of pre-signed transactions to verify the correctness of the calculation.
When a computational error is discovered, the verifier can expose the prover's dishonesty through an on-chain fraud proof. In the BitVM system, if the prover's response is proven to be wrong, they will lose the bet and forfeit their funds. Conversely, if all answers are correct, the prover will keep their funds. This economic incentive mechanism is designed to prevent dishonesty.
Ultimately, this interaction ensures that computational verification is only transferred to the Bitcoin blockchain when disputes arise, thereby performing the vast majority of computations off-chain. This design maintains the efficiency of the Bitcoin network while providing the ability to run more complex programs on Bitcoin.
BitVM Security
From the perspective of architectural design, the security of BitVM is mainly based on the following aspects:
Fraud Proofs
In the event of a dispute, the validator can challenge the proposer's false claims through fraud proofs. This mechanism is similar to Optimistic Rollups and does not require changing Bitcoin's consensus rules.
Challenge-Response Protocol
BitVM uses a challenge-response protocol where the proposer and the validator pre-sign a series of transactions during the setup phase of the protocol. These transactions are used to resolve disputes when they arise.
Off-chain calculation and on-chain confirmation
BitVM allows complex computations to be performed off-chain, and only when disputes arise will the relevant verification and resolution be performed on-chain. This approach reduces the consumption of on-chain resources while maintaining the integrity and security of the Bitcoin blockchain.
Deposit and penalty mechanism
If a proposer makes an incorrect claim, the validator can confiscate their deposit. This mechanism ensures that the attacker always loses their deposit due to incorrect behavior.
Bilateral contract mechanism
This improves privacy on BitVM and reduces transaction costs, but its versatility is reduced compared to EVM's multi-party mechanism.
Nostr Protocol
What is the Nostr Protocol
Nostr stands for "Notes and Other Stuff Transmitted by Relays", which literally means "Notes and Other Stuff Transmitted by Relays". From the full name of the protocol, it is not difficult to see that this is a transmission protocol, and the existence of relays shows that this is not a P2P Transfer protocol. [Github code](https://github.com/nostr-protocol) update records show that this project was launched in November 2020. The protocol aims to create the simplest open protocol for a censorship-resistant global social network. It is a decentralized social protocol that allows users to create, publish and subscribe to any type of content without the control or intervention of any centralized platform or institution. Nostr is inspired by Bitcoin and Lightning Network. It uses similar cryptography and consensus mechanisms, as well as an event-based data structure called Nostr Network.
Nostr Protocol Components
Public-private key pair
A public-private key pair is a Nostr account. Nostr accounts are not based on the traditional username and password system, but use a similarcryptocurrencyThe public key and private key system. For ease of understanding, the public key can be regarded as a username and the private key as a password. It should be noted that once the private key is lost, it cannot be reset like a password. The public key is prefixed with npub1 and the private key is prefixed with npub2.sec1 is the prefix. Before use, make sure that the public key and private key are kept properly, because they cannot be recovered once lost.
Client
Nostr itself is just a protocol for sending information on the Internet. Users need a client software to use the Nostr protocol. The client can be a web page, desktop software or mobile app. The client reads the information from the repeater and sends the newly generated data to the repeater so that other clients can read it. The information contains signatures, which can ensure that the data is sent by the real sender. The client uses a private key to create the signature. The first time you use the desktop or mobile client, you need to store the private key in it. The public key can be obtained from the private key. If you use the web client, it is not recommended to save the private key directly in it. It is better to use a plug-in to save the private key.
Repeater
A repeater can be thought of as the backend server of the Nostr protocol. Nostr clients send information to repeaters, which may or may not store the information and broadcast it to all clients connected to them. It is important to note that repeaters are not static, but rather they can change a lot over time. The Nostr protocol relies on repeaters to store and retrieve data, and if a user feels that their client is slow, it is because the repeater they are connected to is slow, so consider adding some additional repeaters.
NIPs
Nostr 实施标准(A Nostr Implementation Possibilty, 简称 NIP),用来规范兼容 Nostr 的中继器和客户端软件,哪些必须、哪些应当、哪些可以实施。「NIP 」是概述 Nostr 协议工作原理的参考文档。Nostr 是一种去中心化协议,并不被某一个中心化机构所垄断(比如推特)。这意味着协议的发展方向取决于所有参与者,我们可以建议和倡导变革,并对他人提供的想法提供反馈。作为协议社区的积极成员,大家对Nostr 网络的后续发展方向都有一定的话语权。Main code baseNIPs in the repository are approved and new ideas can be added via pull requests.
The following are some of the more important NIPs:
• NIP-04: Message encryption,usesecp256k1 algorithm to complete Diffie-Hellman key exchange, point-to-point encryption
• NIP-05: Mapping public keys to domain names, which is easy to remember. For example, the author's public key is npub10jprg9n3ecjlpez0fyg7y7yvpl66drtjv8rv0hfllxpdxhesuwzs4c2kw6, which is mapped to the domain name @NomandJames
• NIP-06: Mnemonics,andcryptocurrencyThe wallet's mnemonic is similar to
• NIP-13: Proof of WorkThis concept was proposed before the emergence of Bitcoin and is now widely used in the blockchain POW consensus layer and in the Ethereum whisper protocol. Its principle is that before the client sends a message, it must first complete a computationally intensive proof of work, and the relay server that receives the message will verify the validity of this proof. Providing this proof means spending computing power, which raises the threshold for sending spam messages to block relays.
• NIP-22: Message timestamp. Tells the relay server when the message was created so that the relay can selectively receive the message. The timestamp can be set in the past or in the future.
• NIP-40: Expiration time. Tell the relay server when the message will expire so that the relay can delete it.
• NIP-57: Lightning Network Reward Link.
• NIP-65: Recommended list of relay services.
event
Events are the only `Object` structure on Nostr. Each event structure has a category (`kind`). The category is used to mark the type of event (what kind of operation the user performed or what kind of information was received).
How the Nostr Protocol Works
The Nostr protocol works through relays. These relays allow users on the same relay to send Json files to each other.
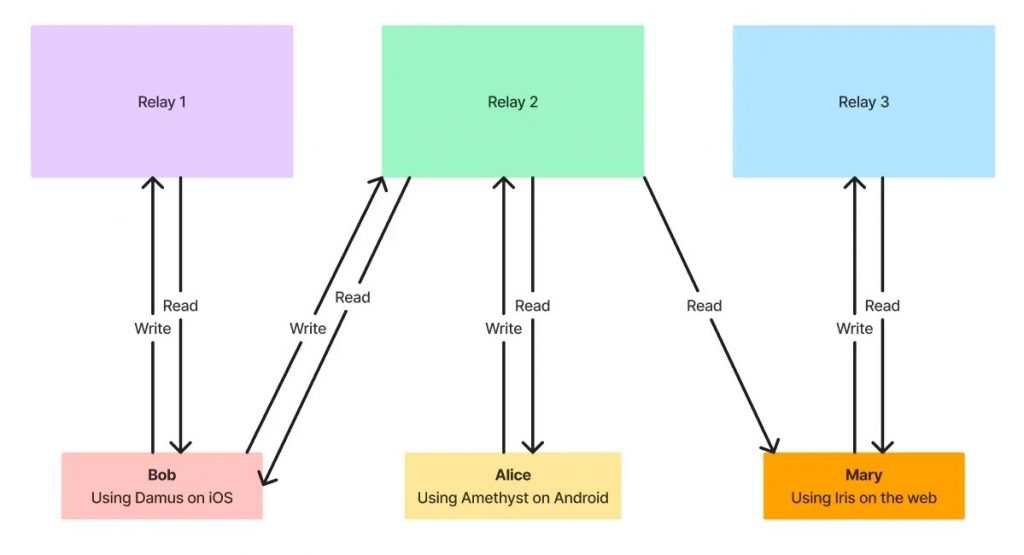
The following simplified graphic examples will help you understand:
The diagram contains 3 relays and 3 users. Each user in the diagram uses a different client (not on the same platform).
The read and write situations in the chart are as follows:
• Bob can see all of Alice’s tweets, but cannot see any of Mary’s tweets (Bob doesn’t even know Mary exists).
• Alice can see all of Bob’s tweets, but cannot see any of Mary’s tweets (Alice also doesn’t know that Mary exists).
• Mary can see the tweets from Bob and Alice. Since Mary only writes to relay 3, she can read from relay 2 (which holds Bob and Alice's data).
A closer look at Nostr contracts
Given that the Nostr protocol is a very lightweight open protocol that provides protocol specifications for decentralized social media platforms, we try to do a simple protocol code analysis:
The basis of the protocol is a WebSocket server (called nostr-relay) that processes and stores a very simple data structure called Event. It looks like this:
{
“id”:
“pubkey”: ,
"created_at": ,
"kind": ,
"tags": [
[“e”, , ],
[“p”, , ],
… // other kinds of tags may be included later
]
"content": ,
"sig": ,
}
Events are always signed (using Schnorr type signatures) and contain structured data that may have different semantic meanings.BIP340The Schnorr type defined in XOnlyPubkeys (currently used with Bitcoin Taproot) is used as “identity” throughout the protocol.
nostr-client is an app that can communicate with nostr-relay and can subscribe to any set of events using subscribers.
FiltersRepresents the set of all Nostr events that are of interest to the client.
Clients do not need to register or create an account, as the client is identified using the user's public key. Each time a client connects to the relay, it submits the user's subscription filter, and the relay streams "events of interest" to the client as long as they are connected.
Relays can cache client subscriptions, but they don't have to. Clients should handle everything "client-side", and relays can be dumb as a rock.
Clients don't talk to each other. Relays do. This allows a relay to fetch data for a client that it doesn't have, and a client can subscribe to events outside of the relay it's connected to.
At first glance, this gives the impression that Nostr is useless as a protocol (why not just sign and dump raw JSON and let the client figure it out?), but looking deeper, the “dumb server, smart client” model can be found to have some huge engineering advantages in decentralized protocol design.
Full decentralization is the main feature of Nostr
As the protocol layer of social applications, Nostr transmits Notes and other stuff through Relay. It does not rely on any centralized server. It is fully decentralized and allows any App application to access freely. It provides an open and permissionless social platform through a distributed network. Therefore, Nostr does not even provide users with C-end products that can be directly operated, but focuses on the necessary infrastructure for social networking at the protocol layer. The productization capabilities are provided by third-party apps. And the social behaviors of users of different apps are interoperable.
Nostr’s advantage is that it provides a truly free and open social network that is not influenced or threatened by any centralized power or interest. Users can freely express their opinions and beliefs without worrying about being censored, banned or cancelled; content creators can freely set their own incentive models without worrying about being deprived of income or unfair competition. Nostr users can also freely choose their own social circles without worrying about being manipulated, misled or deprived of privacy.
Nostr is very different from traditional social media, and it has the following features and advantages:
Decentralization
Nostr does not rely on any centralized server or platform, but transmits and stores information through the Bitcoin network. In this way, users do not have to worry about their data beingstealaccess, review or deletion, nor be subject to the rules or policies of any third party.
Autonomy
Nostr allows users to control their own data and identity. Users can freely choose who they want to follow and trust, and can also freely express their opinions and ideas. Users do not have to worry about being blocked, blocked or downgraded, nor do they have to endure the interference of advertisements or recommendations. At the same time, the authentication of specific users makes it easy for users to identify spam and robot information.
open
Nostr is an open protocol that anyone can participate and contribute to. Users can develop and use different clients themselves, or build and run nodes themselves. Nodes are servers that forward and store Nostr information. Users can also create and use different types and tags themselves, which are metadata used to distinguish and classify Nostr information. The concise and flexible event format supports various types of publishing: social media posts, long-form content, rich media, e-commerce, etc. At the same time, Nostr is combined with the Lightning Network to achieve a new [value-for-value], more fair business model.
Security risks of the Nostr protocol
Private Key Management
The Nostr protocol uses public-private key pairs as accounts, and users need to properly manage their private keys. Once a private key is lost, it cannot be recovered. This may be a challenge for most users because they may not have enough technical knowledge and experience to manage private keys securely.
In the Nostr protocol, users need to select and verify relayers themselves. If users choose an untrusted or malicious relayer, their information may be leaked, tampered with, or deleted.
Information dissemination
In the Nostr protocol, information sent by users is not propagated among multiple relays. This means that if a user's information is not received and stored by enough relays, their information may be lost or cannot be seen by other users.
The island effect is getting worse
In the Nostr protocol, relayers can freely choose whether to receive and store user information. This may cause some relayers to choose to only receive and store information that they think is valuable or in their interest, while ignoring or rejecting other information.
Malicious protocol extensions
The Nostr protocol defines some basic event types and functions, but it also allows clients and relays to selectively implement some additional functions. This may cause some clients and relays to implement some unsafe or malicious functions, thus affecting the security and privacy of users.
Information processing
Since the Nostr protocol does not have a consensus layer, some relays do not process messages with large discrepancies between timestamps and UNIX time, which makes it possible for clients to forge messages by exploiting the time difference.
Nostr Ecosystem Overview
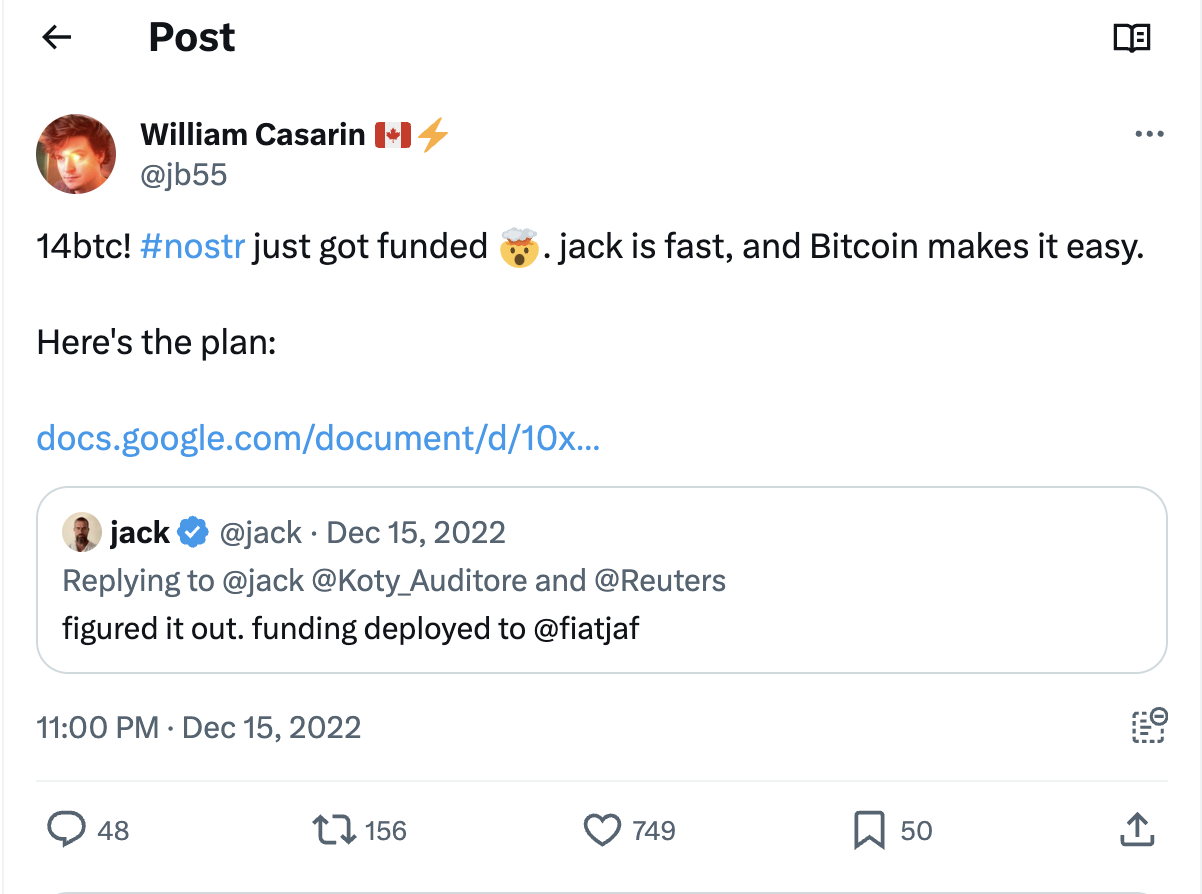
The main supporter of the Nostr protocol is Twitter co-founder Jack Dorsey. As early as December 2022, Dorsey donated 14.17 bitcoins (about US$245,000) to Nostr to support its development. On his X profile, his personal Nostr address is still prominently displayed, which shows his love for the protocol.
Damus⚡️: The main application of Nostr protocol
X:https://twitter.com/damusapp
Damus is a social app that supports Bitcoin tipping based on the Lightning Network. It uses tipping as a way to replace the more common "Like" or praise, and the low fee rate of the Lightning Network makes the network cost of tipping so low that it is almost negligible.
In addition to Damus, other applications of the Nostr protocol include the communication tool Anigma, the text sharing tool Sendtr, and the online chess game Jeste.
TGFB: The main media partner of Nostr agreement
Official website: https://tgfb.com/
TGFB is a Christian Bitcoin education platform whose goal is to educate and equip Christians to understand Bitcoin and use it to promote God's glory and benefit all mankind.
A large part of the podcast is reserved for the content promotion of the Nostr protocol, hosted by Jon and Jordan, which explores the connotation and extension of the decentralized social protocol Nostr from a Christian perspective. Christianity is widely preached in Europe, America and even the world, and Bitcoin, which is well known to all Americans and has passed the SEC ETF, plus the Nostr social protocol built on the lightning network with a huge user base. The combination of the three will bring a large number of Nostr protocol advocates and supporters, which will undoubtedly play an excellent role in promoting the development of the Nostr protocol ecosystem.
Nostr Derivative Protocol
Nostr + Taproot assets
Nostr Assets ProtocolIt is an open source protocol that brings Taproot assets and native Bitcoin payments in Satoshis (Sats) to the Nostr ecosystem, while supporting interaction with other payment protocols including the Lightning Network and Taproot assets.
Once a user introduces assets, they can use Nostr's public and private keys to send and receive them at the Nostr protocol layer. The settlement and security of assets still rely on the Lightning Network. After all, the Nostr asset protocol itself does not issue assets, but only introduces assets to the Nostr asset platform through the protocol.
Nostr Assets uses Nostr messages to control (host) wallets, which helps users better perform basic functions such as transfers/transactions. It is built on Nostr's technology, but it is a completely different protocol from Nostr.
Nostr Assets Protocol's fully managed service means that users deposit their Bitcoin or other assets into a wallet controlled by Nostr Assets Protocol, and then send instructions through Nostr messages to deploy, mint and transfer tokens.
It should be noted that there are certain controversies surrounding the full custody service: Nostr Assets Protocol’s custodial wallet may pose security risks, and users cannot fully control their assets. If the platform is hacked or runs away, users may lose all their assets.
At the same time, after Nostr went online on October 30, a large number of people recharged their assets, and the website was shut down for maintenance many times, which caused users to question the background of its team and the reliability of the project. On November 8, the official account of Nostr Assets Protocol responded to a Chinese comment under a tweet. At present, some users have doubts about the true identity and reliability of the project. And Nostr officials have always been extremely opposed to the token with the same name as the protocol in the extension protocol.
Nostr + Inscription
Noscription is an experimental token protocol based on Nostr that allows users to create and trade brc-20-like tokens on Nostr rather than Taproot assets-like tokens.
Comparison of the three
Agreement Implementation
BitVM places extremely high demands on computing power and is currently only theoretically feasible. RGB is better in terms of commercial implementation and has already been used in many applications. (RGB's technical organization LNP/BP has few developers and is non-profit, so the development progress is slow). Nostr also failed to further promote the protocol application ecosystem due to the bottleneck of Socialfi.
Privacy Protection
Both RGB and BitVM are off-chain calculations, but the RGB protocol means that third parties cannot track the history of RGB assets on the blockchain. Only when users receive assets can they understand the history of assets. BitVM cannot do this. As a social protocol, the Nostr protocol has a high degree of unknowns in the relays that spread information. There may be problems such as information leakage, blockage, loss, and malicious tampering by exploiting vulnerabilities.
BTC Nativeness
Neither RGB nor BitVM requires protocol changes to Bitcoin; Nostr is built on the basis of the native Lightning Network, and both are relatively native, with a smooth development experience.
Security of the protocol
The RGB protocol is executed off-chain, and the sandbox environment ensures data security. The invoice system also ensures data security from the design. From the perspective of interaction with BTC, a model similar to the Lightning Network is used for asset issuance.
BitVM adopts the Rollup model and is also executed off-chain. The characteristics of the virtual machine, fraud proof and challenge-response mode ensure the security of BitVM.
Nostr adopts a repeater model. The ingenious design of information transmission between repeaters and the encryption algorithm make the information in the Nostr protocol secure enough.
In the Web3 industry, there is currently no laboratory that focuses on Bitcoin ecosystem security. The establishment of BTC Security Lab fills this gap and provides professional security support and research for the Bitcoin ecosystem. ScaleBit and BiHelix hope to lead the Bitcoin ecosystem security track, set security standards for the entire industry, and promote the healthy development of the ecosystem.
Ecology and Commercialization
As a social protocol, Nostr Protocol has a larger user base and more traffic than both Bit VM and RGB protocols. Its ecological protocol expansion and application commercialization are more complete than the other two.
The RGB protocol has been released for a long time, and there are many ecological projects at present, many of which are waiting for the release of RGB V0.11.
It has only been a few months since the BitVM white paper was released, and the ecosystem has not yet been established.
In the future, the three-party agreement will give rise to many Dapps in the fields of Socialfi, GameFi, and DeFi, bringing a new wave of popularity to the BTC ecosystem.
特别感谢Ausdin.eth, 0xLayman, Echo, Venus 对本次报告作出的贡献。
*【Disclaimer】The market is risky, and investment should be cautious. This article does not constitute investment advice. Users should consider whether any opinions, views or conclusions in this article are suitable for their specific situation. Invest at your own risk. *
The article comes from the Internet:Detailed introduction to RGB, BitVM, and Nostr
Related recommendations: Autonomy and Automation
Video games are the starting point for autonomous worlds, not the destination. Written by: Neilson Translated by: KaiKai & GINK, AW Research You need to be a world maximalist to automate your autonomy. Development emerges, creates emergencies, NPCs,AIYou need to laugh at people who have an “I kind of get it” perspective. …