Was it stolen before you even made any money? Please keep this inscription anti-fishing guide.
Written by: BlockSec
As the popularity of the inscription concept has reached an unprecedented high, the price of head inscriptions has increased by as much as several billion.Ten thousand times moreIn this context, many people have long been waiting for opportunities to use the complexity and novelty of inscriptions to commit various frauds, and this phenomenon is becoming increasingly rampant.SafetyIt poses a serious threat and has an adverse impact on the healthy development of the entire inscription ecosystem.
To this end, we sorted outThree typical inscriptionsSafetyCase,IncludeScam project risks, risk of mistaken transfer and burn, risk of centralized tools, and as a user, what are the corresponding preventive measures in these scenarios.
Scam Project Risk
In the current Bitcoin protocol, for projectsXiaobai NavigationThe identification of a project mainly depends on the project name specified in the deployment operation, and is identified in the indexer through a unique ID. However, for ordinary users, they can only remember the name of the project and use it as the basis for transactions.This name-based transaction method is risky because there are a large number of similar but different strings in ASCII code, which provides opportunities for visual fraud.Malicious parties can use these similar but different strings to deceive users into thinking they are transacting with a well-known project and issue large amounts of tokens of similar projects.Token.
这种欺诈行为常常发生在项目铸造(mint)的过程中。恶意方会引导用户支付费用,以获取代币或其他虚拟资产,但实际上这些代币可能是没有真实价值的。这种欺诈行为不仅损害了用户的利益,还可能造成整个生态系统的不稳定。
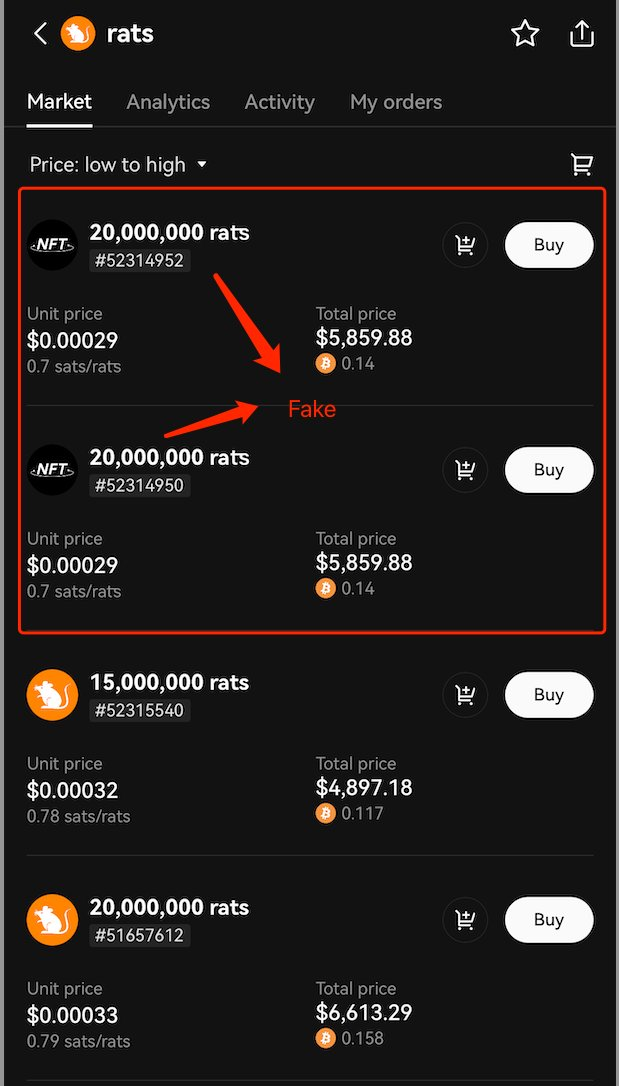
Here we give an example of fake rats. The fake rats and real rats are named very similarly because similar ASCII codes are used. If users do not carefully identify the naming (note the "t" in rats), they will be misled into buying fake rats tokens, causing financial losses.
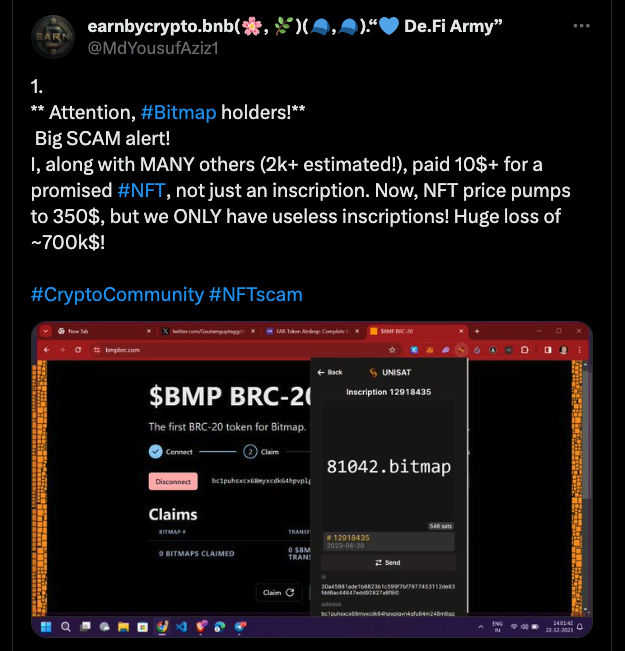
In addition to fake inscriptions, some scam inscriptions even defraud users of additional funds during the minting process.
For example, as shown in the figure, when casting the inscription on the bitmap, the fraudulent webpage also requires the user to pay to an address. If the user does not pay attention to the amount of the payment, he will suffer a significant loss.
Countermeasures: Avoid casting inscriptions from unknown sources
There are many different ways to cast inscriptions now. The types we have come into contact with are:
-
The project's own distribution website
-
Unisat, etc.walletAuxiliary tools
-
Other auxiliary tools provided by third parties
这些不同种类的铭文铸造渠道,会让用户陷入迷茫,无法分辨渠道的正确性和安全性,从而陷入 scam 铭文的欺诈陷阱。这里我们It is recommended that users use morewalletUse the official issuance website of the project party to cast inscriptions. Try to confirm the correctness of the website before casting the inscription, and carefully observe the required casting amount.If it is a large batch mint, weIt is recommended to use wallet auxiliary tools to further increase the security of funds.
Risk of wrong transfer and wrong burn
First, mis-transfer refers to the situation where the carrier of the inscription is used as a normal Bitcoin for transfer. Since the inscription is attached to the Bitcoin transaction, for traditional BTC wallets, it will not consider the added value brought by the inscription, and only display the value of the Satoshi locked in the UTXO model.Some users may perform traditional transfer operations without fully understanding the inscriptions. This may cause the wallet to mistake the inscriptions for ordinary Bitcoin assets and merge and split them with other UTXOs and send them to the wrong address, resulting in irreversible losses.
Secondly, accidental burning refers to the situation where the inscription is burned or deleted as worthless or meaningless information. Since the inscription does not directly affect the ownership or value of Bitcoin in the split model, some users may mistakenly believe that these Bitcoin paper assets with inscriptions are of low value, unimportant or invalid, and choose to merge them with other UTXO models. This may lead to the permanent loss of important information or assets related to the inscription.
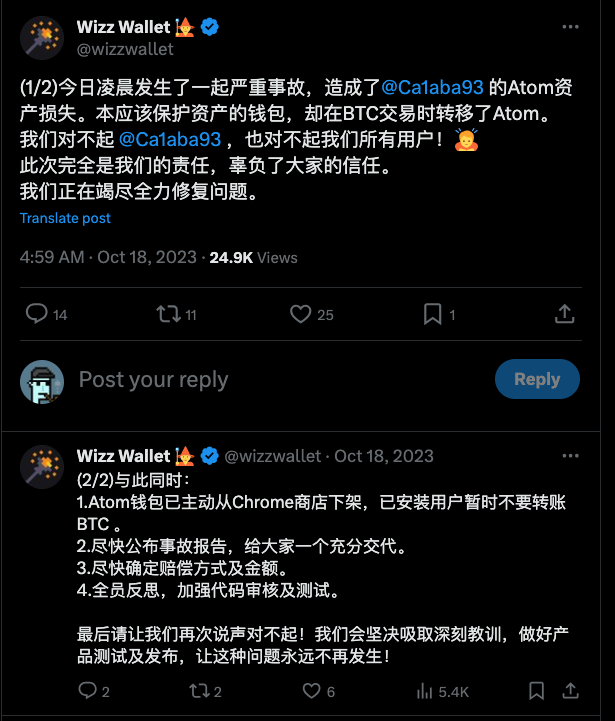
For example, as shown in the figure, in a BTC transaction that should have protected the inscription, the wallet mistakenly did not recognize the inscription and transferred it as dust, causing losses. https://twitter.com/wizzwallet/status/1714385677985661245?s=20
Countermeasures: Prepare a dedicated inscription address and wallet
In the split model, in order to prevent users from mistakenly transferring or burning high-value inscription assets,Users are advised to prepare dedicated inscription addresses and wallets.This approach can effectively reduce the risk of misoperation and ensure the security of inscription assets. This address should be distinguished from other regular transaction addresses to avoid confusion with ordinary Bitcoin transaction addresses. By isolating inscription transactions from other transactions, users can better control and manage inscription assets.
Centralized tool risks
BlockchainThe decentralized design allows users to directly participate inBlockchain生态中来,但由于直接使用复杂的 rpc 协议加入区块链生态是一件过于复杂的事情,所以绝大多数的用户选择依赖辅助工具从而参与到铭文生态的铸造,交易过程中。
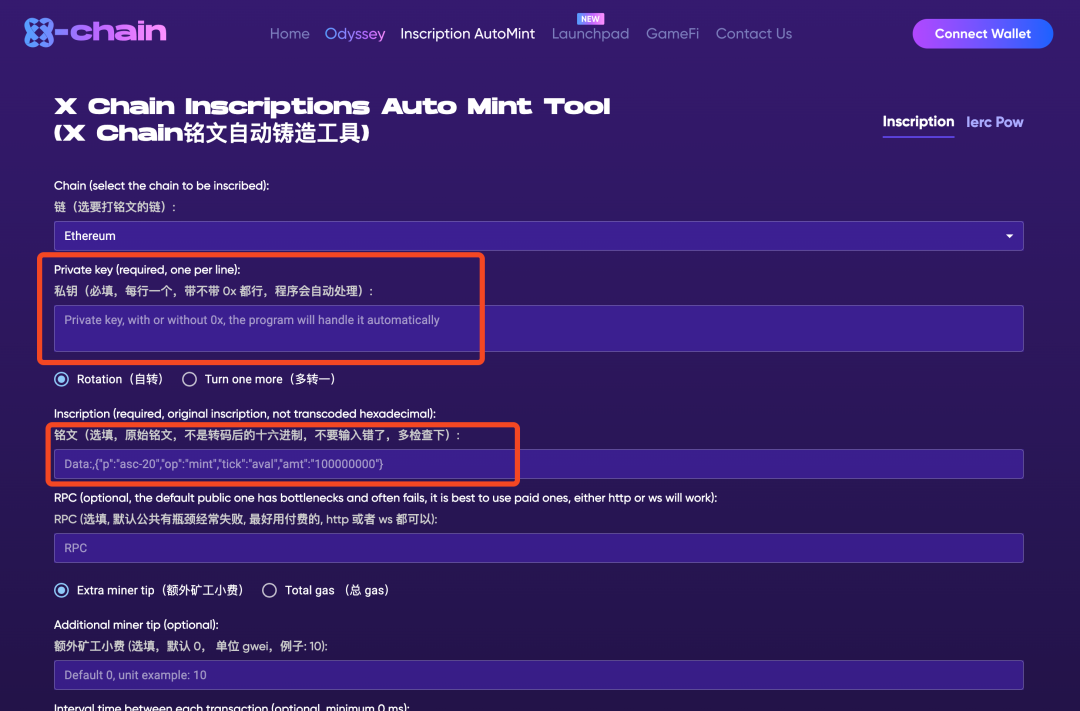
Since inscription is a new concept, its ecology is still in its infancy compared to the mature ERC20 system. Although auxiliary tools have sprung up, most of them focus on functional implementation, and there are still some omissions in security considerations. For example, users are directly asked to import private keys for proxy signing, and users are asked to entrust assets to the platform to realize transactions.These operations expose the user's private key, and the centralized tool essentially controls all the user's assets, which is prone to centralized risks such as rug.This type of risk is similar to that of some wallet companies, which, after obtaining the user's private key, secretly take away all the user's assets and then declare the company bankrupt.
For example, the following proxy tool obtains the user's private key and directly transfers the money in the walletstealWalking.
Countermeasures: Use safe inscription assistance tools
In order to improve the security of inscription assets,Users should trade and operate in well-known inscription markets.
For example:
Geniidata: https://geniidata.com/Ordinals/index/brc20
Ordiscan: https://ordiscan.com/
Etch Market: https://www.etch.market/market
These widely recognized inscription exploration and market platforms provide a safe trading environment and reliable inscription information. Minting, trading, and other operations of inscriptions on these well-known platforms can increase the security of users.另外,用户应保持警惕,不要盲目相信不知名的网站提供的铭文铸造和交易服务。在进行任何操作之前,应仔细研究并确认网站的信誉和安全性。此外,用户还要确保不向任何不受信任的第三方透露自己的私钥或其他敏感信息,以防止遭受钓鱼或stealstealBehavior.
Summarize
After a deep understanding of the risks of inscription scams, mis-transfers and mis-burns, and the potential threats of centralized tools, we can find that although the inscription ecosystem is full of prospects and possibilities, it is also accompanied by many risks and challenges. Users must be highly vigilant and cautious about the transactions and storage of inscriptions. From using official channels to cast inscriptions, preparing dedicated inscription addresses and wallets, to choosing safe inscription auxiliary tools, these precautions can greatly reduce risks and protect the safety of users' assets. Finally, we encourage all users to be cautious when participating in the inscription market. In the world of digital assets, safety always comes first.
The article comes from the Internet:Was it stolen before you even made any money? Please keep this inscription anti-fishing guide.
Related recommendations: A tour of BTC ecosystem expansion plans: BitVM, the art of etching
比特币网络上智能合约是如何实现的? 撰文:Simon shieh 前言回顾 上一篇《BTC 生态扩容方案巡礼:铭文何去何从》中,我们讨论了热门的铭文生态的技术原理和可能存在的安全问题,并且提到了用递归铭文来实现智能合约的可能性。但是因为 Luke 对 Tapr…